Planisys Multi-Factor-Authentication (MFA)
Planisys provides Multi-Factor Authentication (MFA) to access PDNS. This system adds an additional layer of security after entering the email and password. You can choose between two authentication methods or both:
Google Authenticator (or any TOTP - Time-based One Time Password application).
Google Authenticator (or any TOTP - Time-based One Time Password application).
Important
It is recommended to have both enabled, although only one is needed to log in, in case the mobile device is lost or access to the email account is lost.
Importance of 2FA in PDNS
The information stored in PDNS is critical for the operation of practically all services managed by the user. For this reason, it is important to implement a second authentication step after entering the username and password.
Although the control panel uses encrypted HTTPS, protecting credentials from potential attacks on Wi-Fi or wired networks, there are additional risks associated with the user’s device. For example, if a device is compromised with a keylogger, the attacker could capture the login credentials. However, with a second factor like TOTP or email, access remains secure because the attacker would need to bypass this additional step.
Advantages of MFA
Google Authenticator: - Generates 6-digit codes that constantly change over time (TOTP). - It is a highly secure option because the codes are synchronized with time and do not depend on the network.
Email: - You will receive a unique code via email each time you log in. - The MFA email does not have to be the same as the one you use to log in; you can configure a different one.
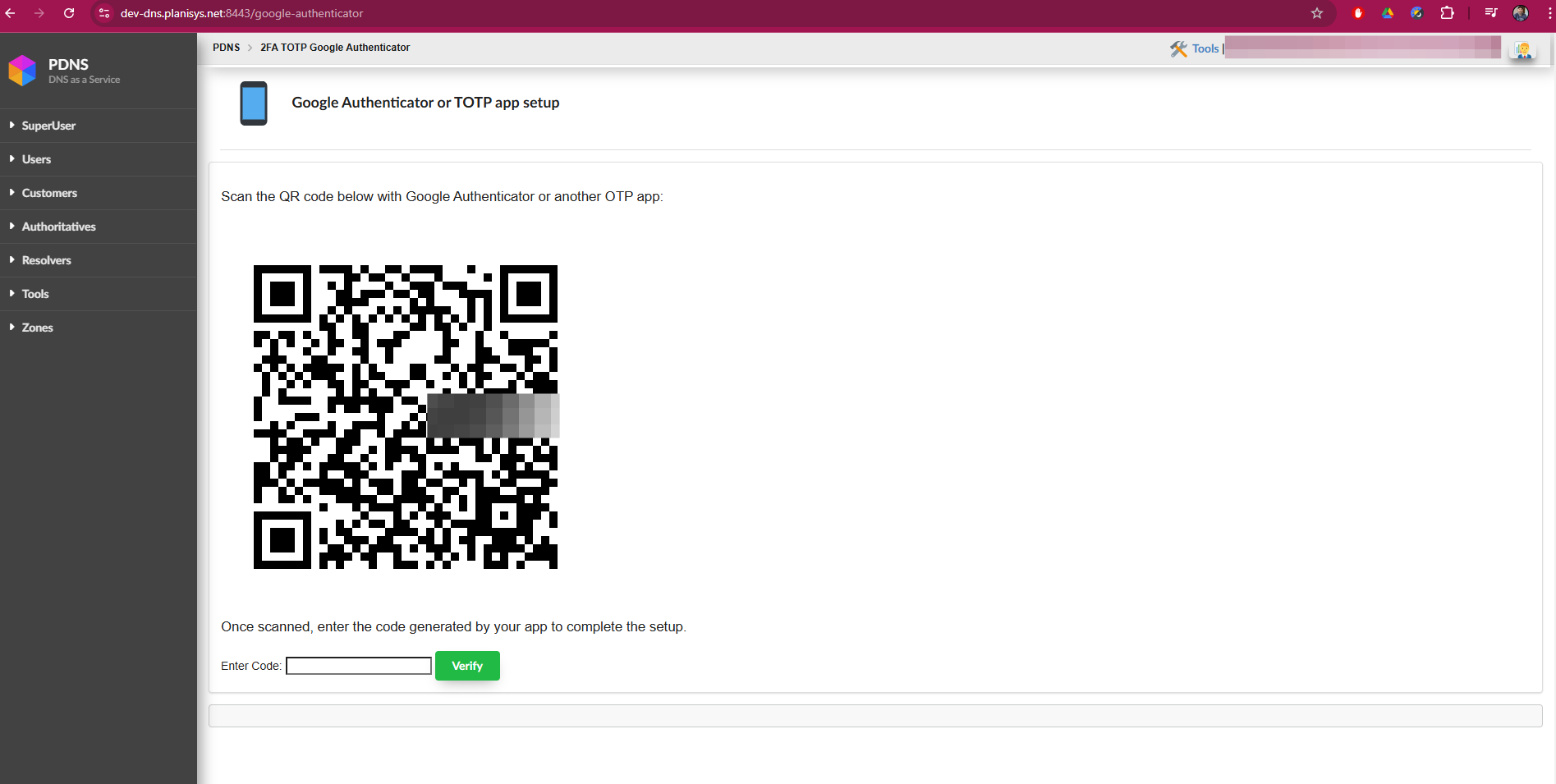
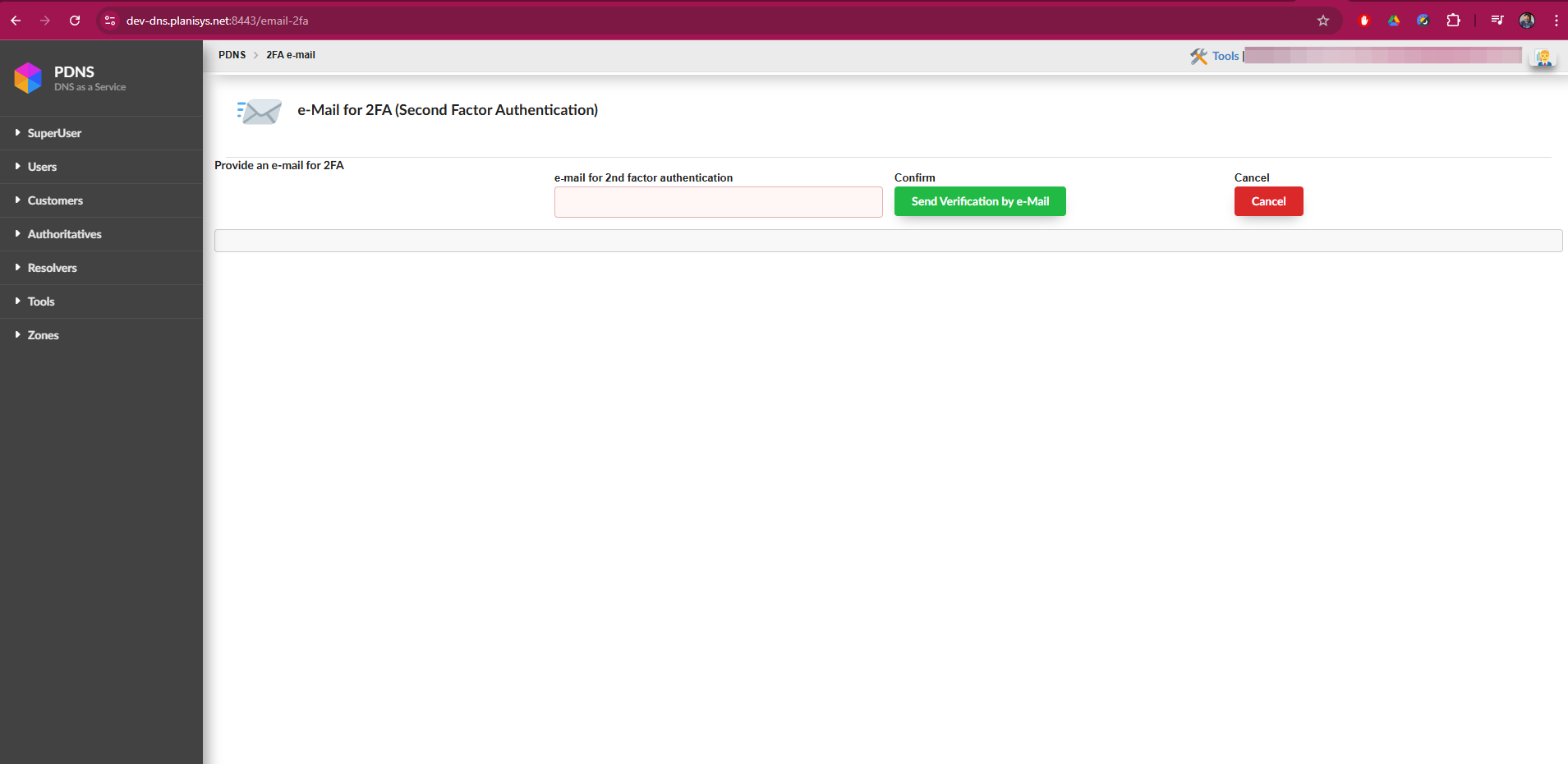
Recommended Configuration
It is recommended to configure both MFA methods (Google Authenticator and email) for greater flexibility. The system will only request one of them after login, depending on the user’s preference.
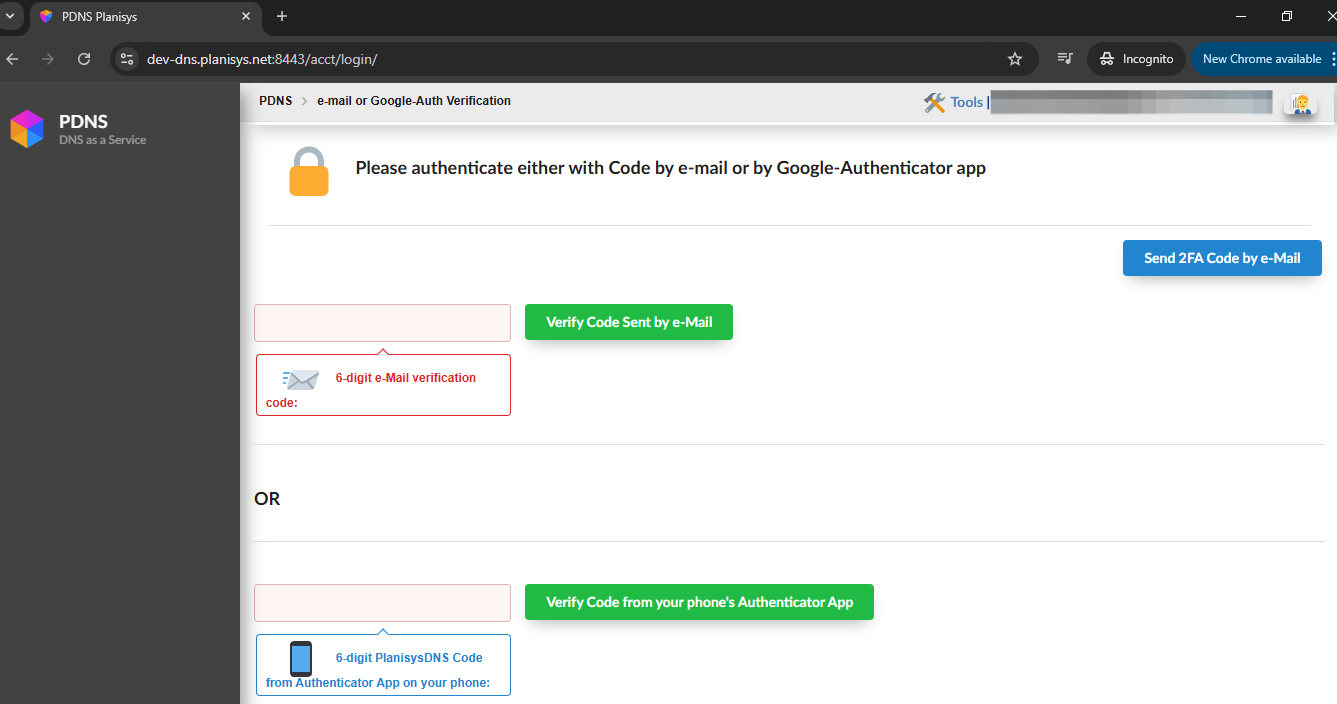
In case of an error when entering one of the 6-digit codes, the user will be redirected back to the login screen.
Special Cases
Loss of access to 2FA email: - If the 2FA email becomes inaccessible, you can use Google Authenticator as an alternative. - You can deactivate the 2FA email from the corresponding screen and register a new one.
Loss of access to mobile device: - If you lose access to your mobile device or need to migrate to a new one, you can use 2FA email. - To reconfigure Google Authenticator, delete the TOTP code from the corresponding screen and scan a new QR code.
Behavior with IP or browser changes
It is important to note that accesses via second factor are recorded with:
Timestamp (time mark).
IP address.
Browser identification.
If the user changes their IP address or browser, the system will mandatorily request the second factor, even if a different period (such as once per week) has been configured.
Final Comments
In PDNS version 2.2.2, other second-factor authentication methods are not implemented, such as:
Passkeys (fingerprint from the device keyboard).
USB or NFC hardware devices, such as Yubikey or Nitrokey.