Requirements for on-premise resolvers
Planisys will prepare on-premise servers to be part of its infrastructure linked to a PDNS Reseller or Tenant.
Note
A Debian 12 server must be installed in English with UTF-8 locale. Do NOT install any packages, and, unless company policy requires otherwise, do NOT install a firewall.
Warning
Planisys will handle the installation and hardening of the server once it has been handed over with root access.
If there is an external firewall
Access must be allowed from the IPs 190.185.104.222, 209.127.217.3, 190.185.104.132, 190.185.107.248, 179.63.248.252, 179.63.248.250, 179.63.248.92, 2803:bc00::81 on ports 22022 and 53 (incoming), at a minimum.
Then the resolver server must always keep the following incoming and outgoing ports open to the public:
53 TCP/UDP - standard DNS
853 TCP - DoT (RFC 7858)
443 TCP - DoH (RFC 8484)
8443 TCP outgoing, connection initiator
TCP 80 if no certificates are available, for Let’s Encrypt ACME HTTP-01 challenge
TCP 22022 for SSH instead of default port 22
Application-level access restrictions on ports 53/853/443 will be defined according to the networks declared in the PDNS web interface. If the client wants to replicate those restrictions at the firewall level, they may do so, but doing this would cause the SIEM data to be lost if it were to be used.
Locale
Debian locale must be set to en_US.UTF-8, and installed in US English
Hardware selection for a resolver
Since the resolver must compute DNSSEC hashes every time it resolves a domain from the root nameservers, it is important to choose suitable hardware.
For this, we recommend running the following command on Linux:
grep -o -w 'aes|sha\_ni|pclmulqdq|rdseed|rdrand|avx|avx2|avx512' /proc/cpuinfo | sort | uniq
The ideal result in 2024 would include the following flags, taking into account SIMD (Single Instruction Multiple Data, or parallel batch processing):
sha_ni (DNSSEC hashing: DS/NSEC/NSEC3 in SHA-256)
aes (for DoT/DoH)
avx (ideal for batch validation)
avx2 (ideal for batch validation)
pclmulqdq (helpful in DoT/DoH)
rdrand (DNS cookies, NSEC3 randoms)
rdseed (RNG, source of entropy)
avx512 (for large-scale SIMD, high-capacity resolvers)
Hardware requirement scale
Up to 20,000 clients 2 x VPS with 16GB RAM / 4 vCPU / 20GB SSD
Up to 100,000 clients 2 x VPS with 32GB RAM / 8 vCPU / 30GB SSD
Up to 500,000 clients 2 x VPS with 64GB RAM / 16 vCPU / 40GB SSD
Warning
If setting up the VM in a PROXMOX environment, the CPU model must be set to HOST to leverage hardware crypto-acceleration for DNSSEC operations (“CPU passthrough” mode). This can be seen in the following screenshot:
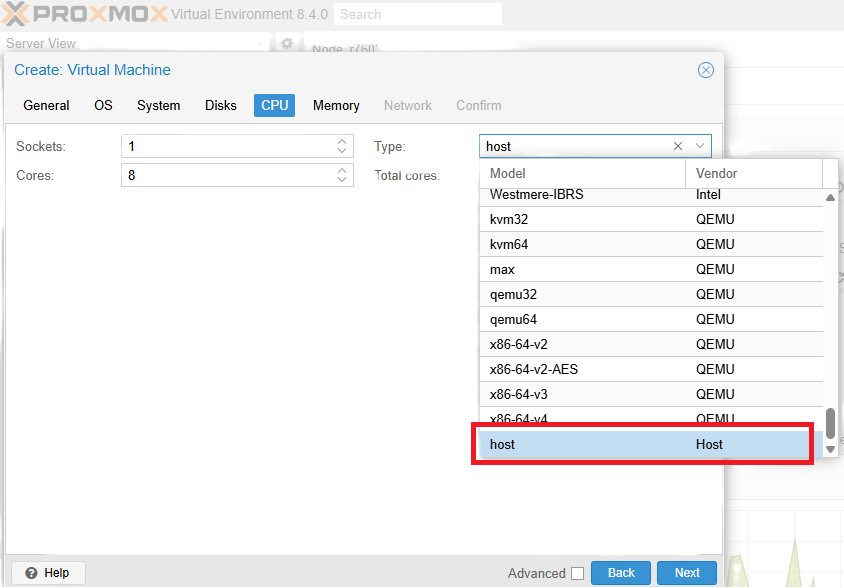
There are several installation methods
If access is provided to a Dell iDrac with public IP, a user and password will be needed so that Planisys can install the Operating System directly on the bare metal and perform all the steps from point 2 without involving the client.
In this case, the firewall must be completely open to the public:
TCP 443 # HTTPS Web UI and Redfish
TCP 5900 # Virtual Console (KVM)
TCP 5901 # (sometimes used by KVM viewer)
UDP 623 # IPMI over LAN
TCP 22 # Optional SSH access
TCP 5120 # Virtual Media (if needed)
Once the installation operation is complete, all these ports may be closed again. It is recommended to place the iDrac IP in a DMZ or internal LAN.
If you already have a bare-metal, KVM, or LXC instance installed, the requirements are:
The operating system to be installed by the client must be Debian12 headless (no graphical interface), with SSH access on port 22022 using a username and password. Later, Planisys will log in as root using a public key.
If a user other than root is provided, it must be able to escalate privileges to root via sudo (or su - root if the root password is available).
This way, Planisys will be able to access the system remotely as root, perform manual operations like ssh-keygen, add IPs to /root/.ssh/authorized_keys, generate a new machine-id, and run an Ansible playbook to set up the resolver.
Additionally, the public IP address must have a reverse DNS entry, and that reverse must resolve back to the public IP. This applies to both IPv4 and IPv6.
Warning
Port 22022 must be open to the IPs listed above. Once the installation is complete, port 22 may be closed again if an external firewall is in place.
The client can follow these tutorials to create the VM. Installation can be done via an .iso image or using cloud-init.
If a VRRP cluster of two or more resolvers is contracted, only bare-metal or KVM setups will be allowed (no LXC), and a virtual IP address must also be provided. Everything else remains the same. The cluster will work in hot/standby mode at the network level, but will use dnsdist for application-level load balancing as long as both servers are operational, thus utilizing the full computational power of the cluster.
If a SIEM has been contracted, Planisys must estimate the data volume to assess which hardware is appropriate. The client must also specify whether they want the SIEM database clustered or not. A local SIEM near the resolvers is recommended to transfer DNSTAP (compressed DNS logs) batches to the database consumer without needing external bandwidth.
Processing Capacity
Warning
Each bare-metal server, up to a Dell R640, can handle a maximum of 4 million queries per second using NVMes and 256 GB of RAM.
An equivalent server, also using NVMes for logs, can handle up to 2 million queries per second with NVMes.
Note
Virtualized KVM servers must use CPU passthrough to take full advantage of the physical server’s instruction set (IS). They are used for setups handling less than 2 million QPS (Queries Per Second).
Application security
Warning
Planisys does not run any web server that requires WAF protection. Port 80 is only opened for a few seconds once a week to renew Let’s Encrypt certificates if the provider does not have TLS certificates, which are required for DoT and DoH.
Warning
The SSH service runs on port 22022 and is protected by fail2ban against brute-force attacks. Accounts do not use passwords (only initially during installation), and access is only allowed via public keys. Brute-force attacks have no chance of success and cannot exhaust server resources.
Warning
No firewall is needed on ports 53, 853 (DoT), or 443 (DoH), as allowed networks are configured from the PDNS console. The software reacts with exponential firewall backoff if someone attempts to use it persistently as an unauthorized resolver. It’s important to understand that the exponential backoff applies to the entire /24 of the offending IP. Therefore, it’s critical to define allowed networks carefully and not leave any out.
Last Updated on 2025-07-14