PDNS Deployments
En esta sección se presentan distintas modalidades de despliegue según los requerimientos del cliente en cuanto a carga y servicios.
Dado que el producto es Multi-Tenant, también está orientado a empresas que manejan múltiples dominios sin requerimientos particulares en infraestructura propia.
DNS for End Clients in the Planisys Cloud
En el Cloud de Planisys se provee la aplicación PDNS-APP como servicio SaaS.
Warning
En esta sección se describen únicamente las acciones posibles por un usuario cliente, sin importar la infraestructura del despliegue.
Los clientes acceden vía web a:
https://pdns-app.planisys.net:8443
Con un único nivel de rol donde pueden:
Crear zonas (Master, Slave, Reversas IPv4 e IPv6)
Crear Registros de Zona (RRs)
Usar la API con su propia APIKEY para automatizar tareas
Esta modalidad es un servicio compartido, donde Planisys provee los servidores autoritativos acreditados en ICANN que el cliente debe usar para delegar sus dominios.
Acceso a los Registros
Los tipos de zonas que un cliente final puede crear son:
Tipo |
Descripción |
|---|---|
Master Directa |
Zona estándar |
Master Reversa IPv4 |
Resolución inversa para IPv4 (PTR) |
Master Reversa IPv6 |
Resolución inversa para IPv6 (PTR) |
Slave de master externo |
Replica de una zona delegada a un servidor externo |
Acciones disponibles en una zona:
Acción |
Descripción |
|---|---|
Consultar WHOIS |
Ver fecha de vencimiento y datos relevantes |
Ver Status de delegación |
Identificar si la zona está activa o con errores |
Acceder a registros |
Botón |
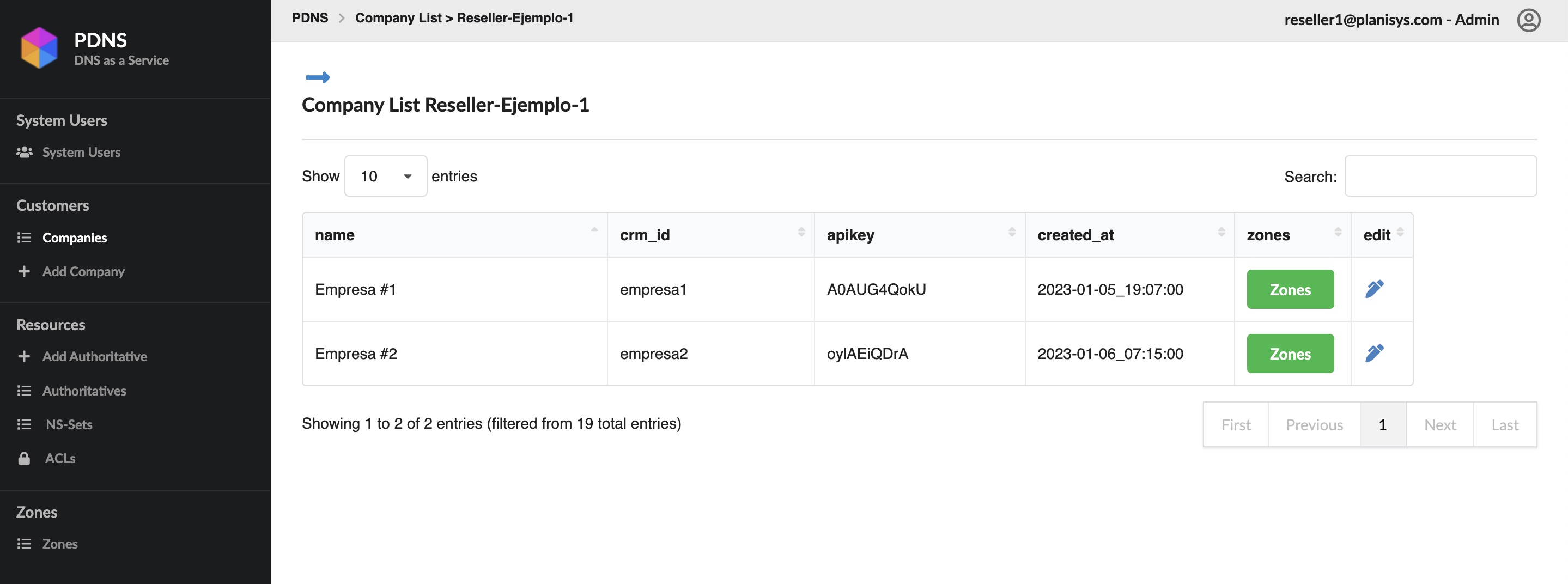
Zone Records (Resource Records)
Tras crear una zona, el sistema asigna automáticamente:
Dos registros
NSdelNS-SETUn registro
SOAcuyo número de serie se muestra arriba
Cada cambio en registros (agregar/editar/eliminar) produce un:
Incremento automático del SOA Serial Number
Ejemplo de vista (reseller mostrado, experiencia equivalente para cliente final):
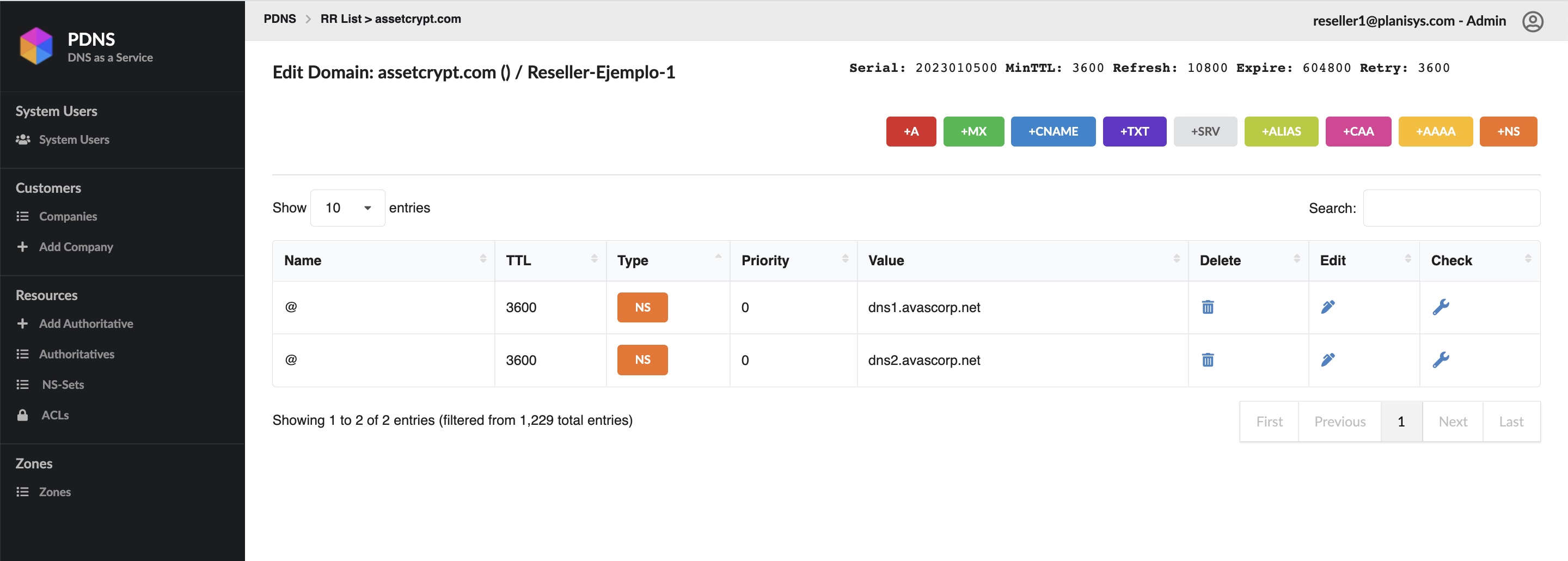
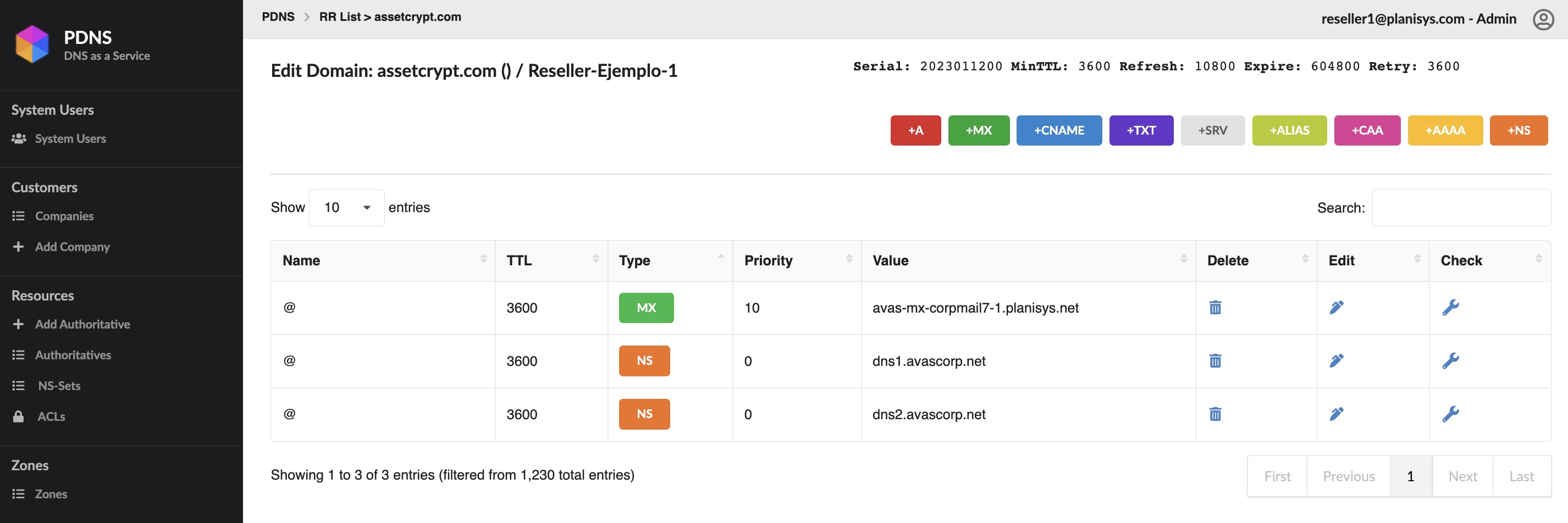
Al agregar un registro MX se observa la modificación del Serial:
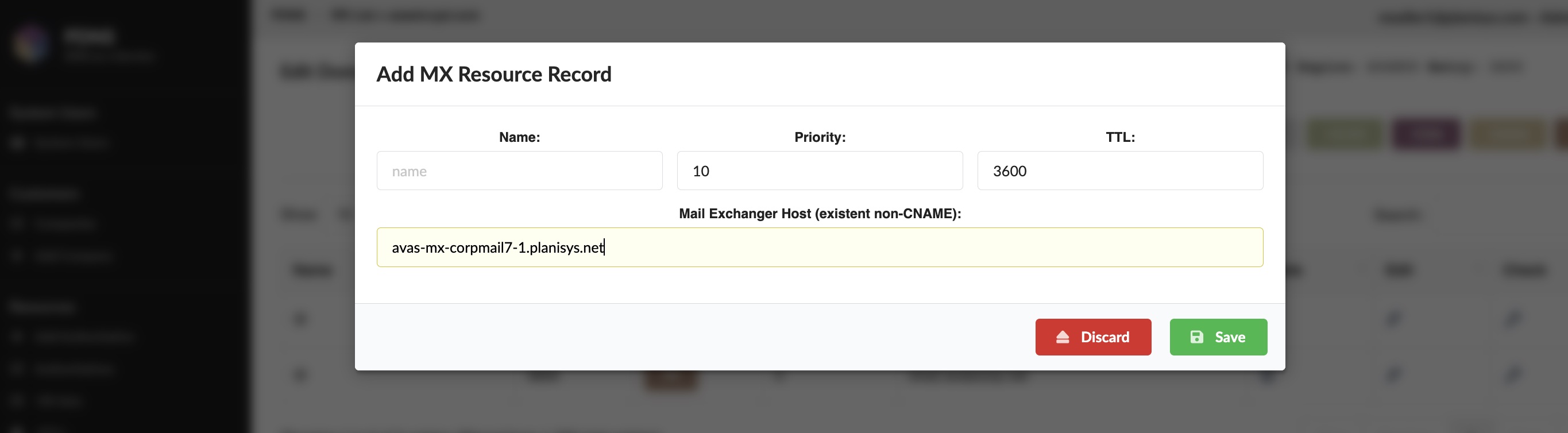
Vista luego del cambio:
DNS para Revendedores / Tenants en el Cloud de Planisys
Un Revendedor / Tenant es una entidad con su propio:
NS-SET (autoritativos propios)
Opcionalmente sus propios resolvers recursivos
Acceden con un login distinto al del cliente final:
Permisos posibles:
Acción |
Descripción |
|---|---|
Crear Empresas |
Organizaciones clientes en el panel |
Crear Usuarios de Empresas |
Cuentas operadoras internas |
Crear Dominios |
Declaración de zonas DNS |
Declarar autoritativos |
Nombres de servidores propios |
Declarar bloques CIDR |
Restringir resolvers para consultas |
Declarar ACLs externas |
Control de zone transfer entrante o saliente |
Zone Management
Puede acceder directamente a las zonas DNS de sus empresas:
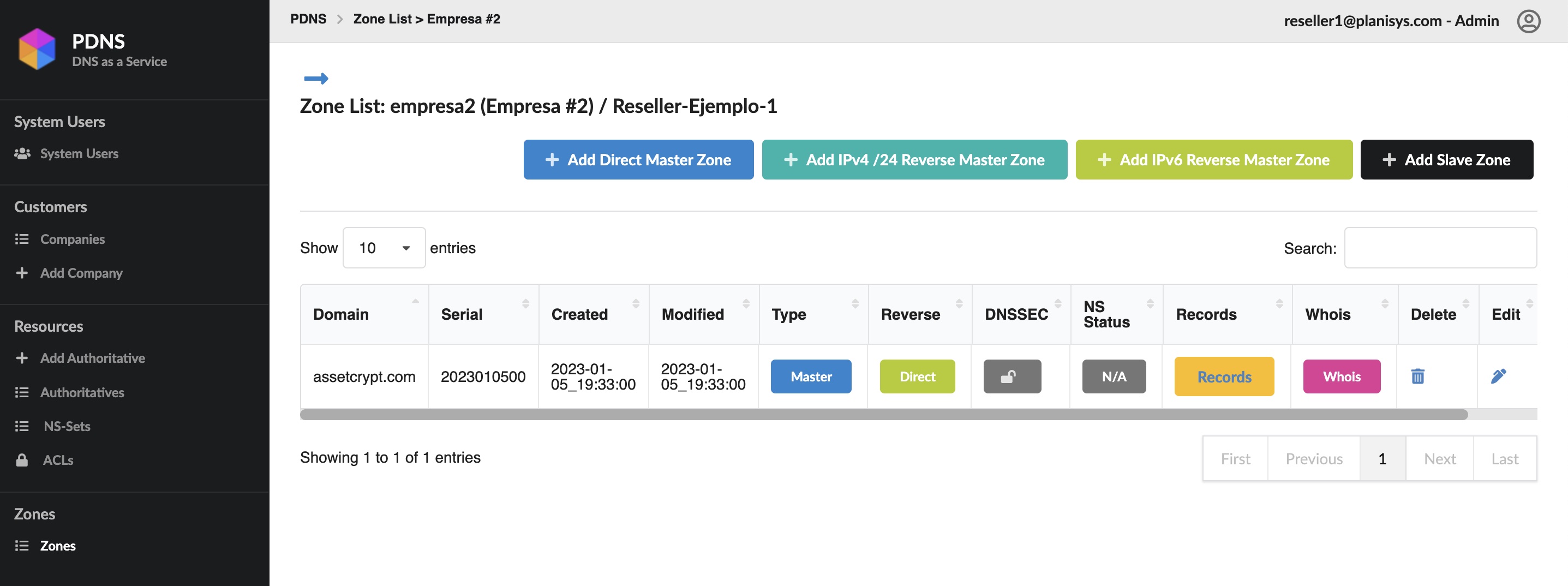
Warning
Si existen dominios no asociados a ninguna empresa, debe crearse una empresa “ficticia” para poder administrarlos.
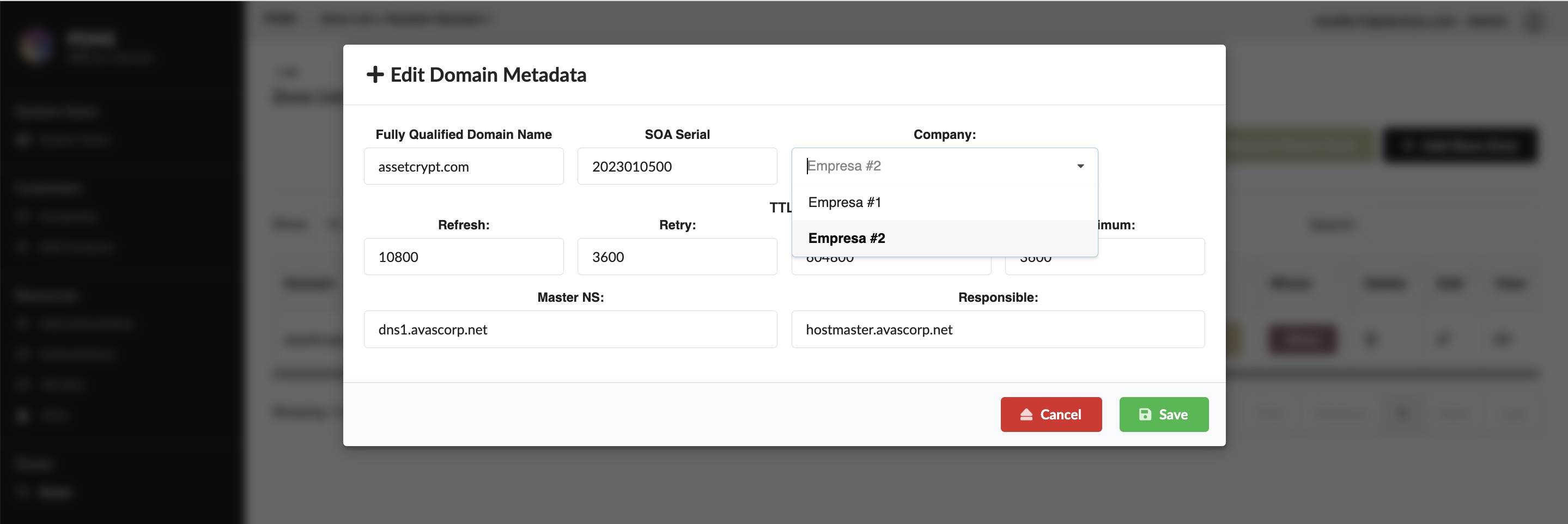
Cambio de titularidad (Mover zona a otra empresa)
Desde la lista de zonas → ícono lápiz → cambiar empresa → “Salvar”
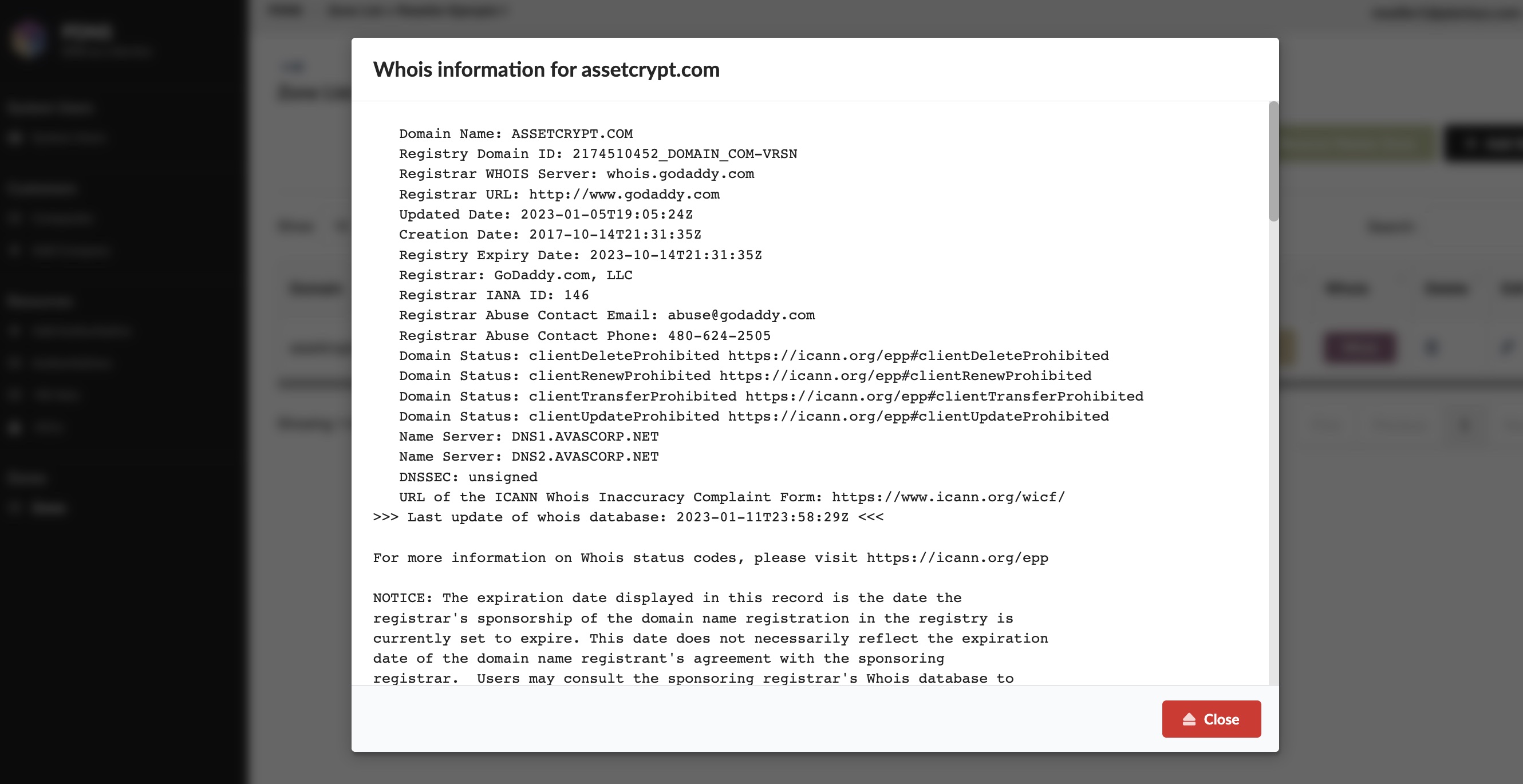
Determinar ownership con WHOIS
El botón WHOIS permite ver datos del dominio, incluyendo vencimiento:

Ejemplo de contenido WHOIS:
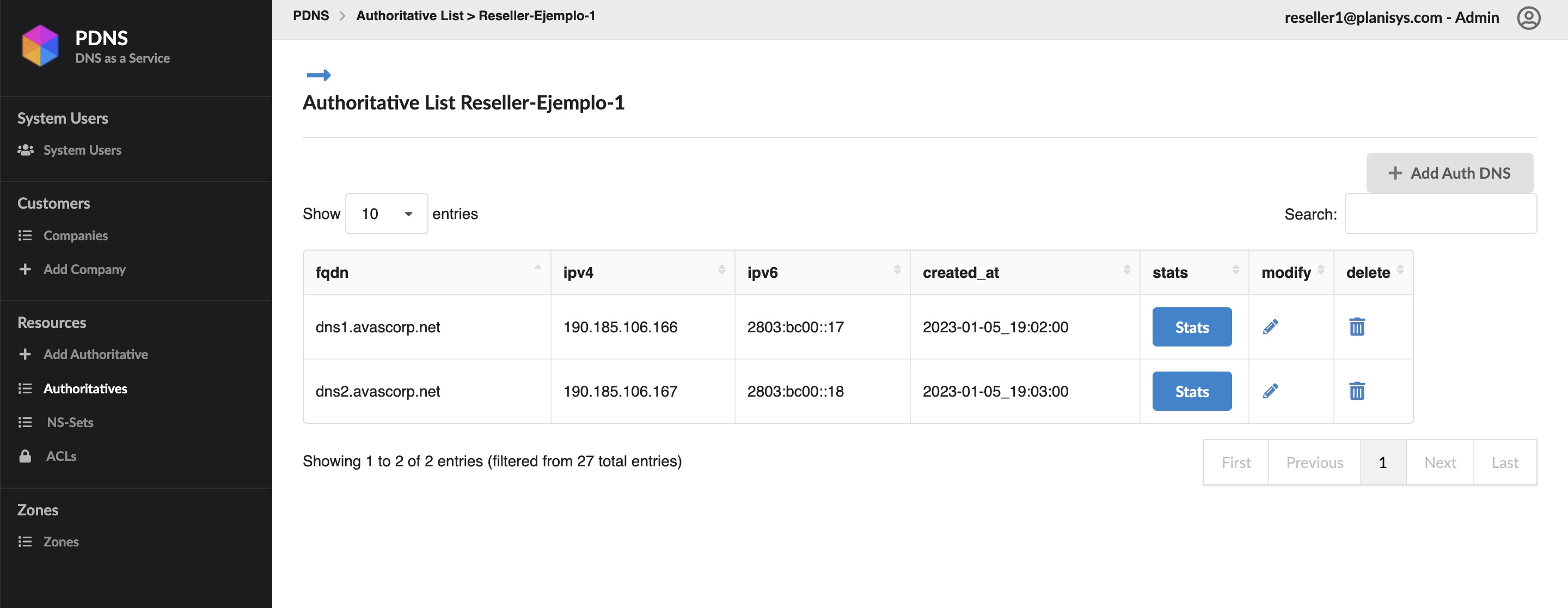
Autoritativos del Tenant
Ejemplo de lista de autoritativos propios del Tenant:
Note
Aunque la aplicación PDNS corra en el Cloud Planisys, los autoritativos y resolvers pueden estar alojados en cualquier nube (AWS, Azure, GCP) o infraestructura on-premise.
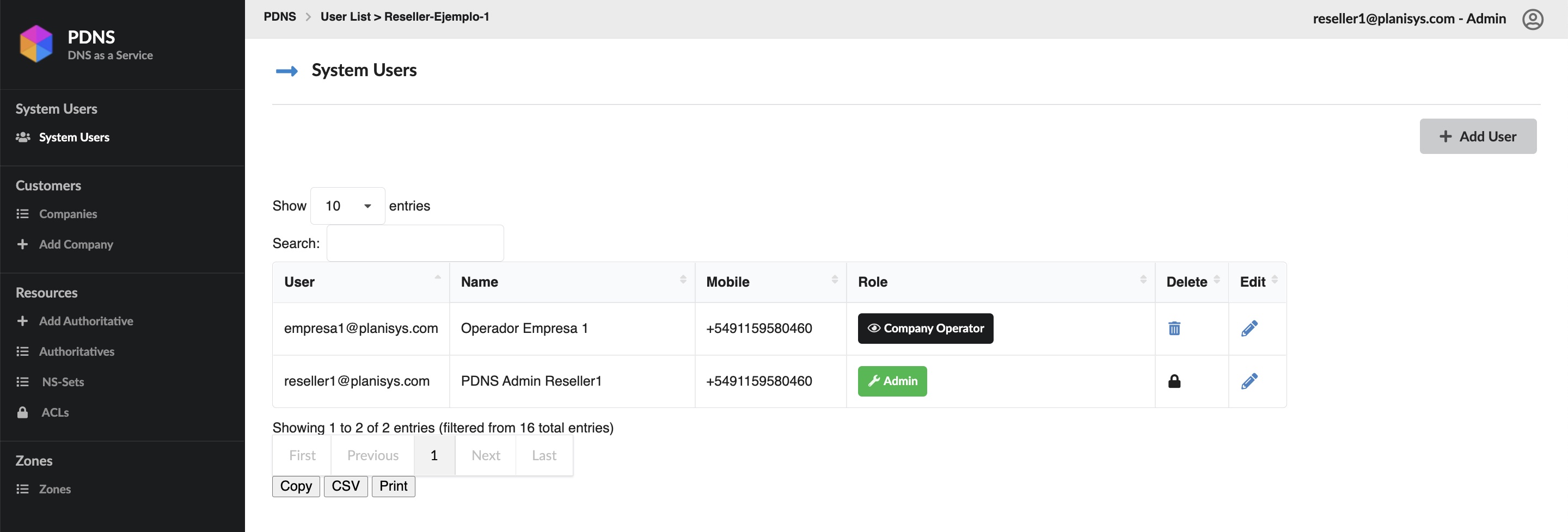
Alta de usuarios
Creación de usuario para una Empresa Cliente:
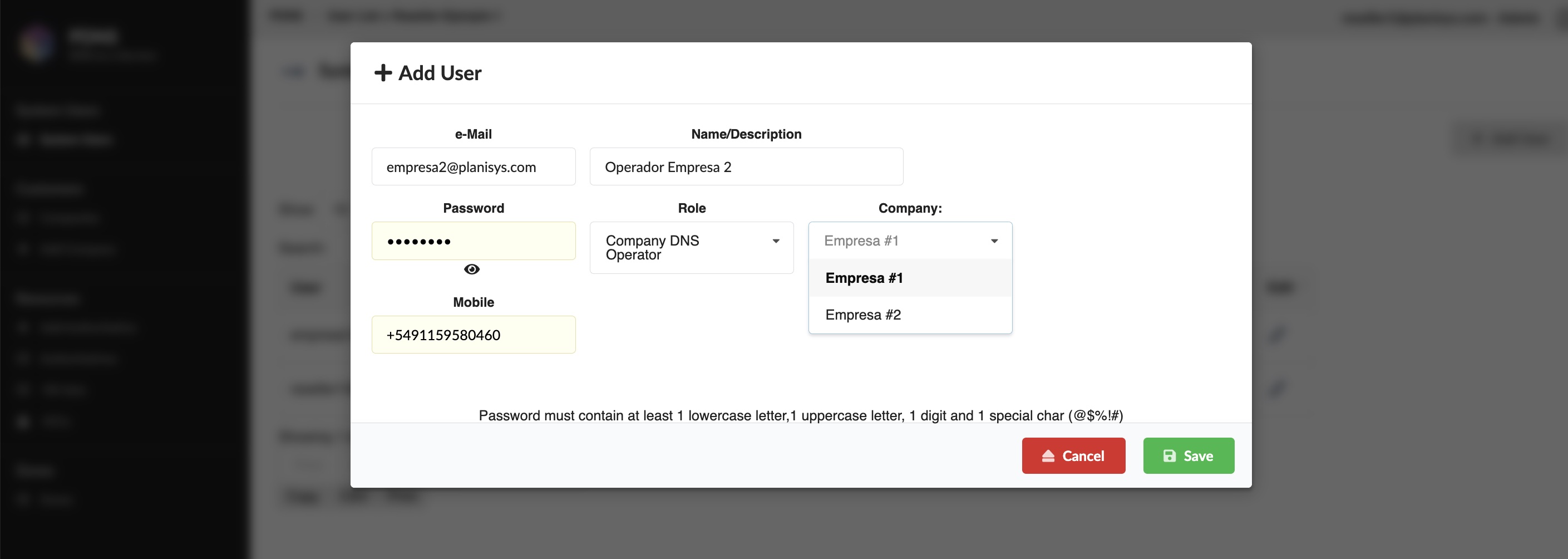
Creación de Operador DNS a nivel Revendedor:
Despliegue On-Premise (Cliente)
PDNS-APP puede desplegarse fuera del Cloud Planisys, alojado en infraestructura:
VPS corporativos
Bare-metal
Cloud local del cliente
Mixto (on-premise + cloud público)
Requisitos mínimos (single-VPS)
Especificación |
Capacidad sugerida |
|---|---|
16 GB RAM – 4 vCPU |
1.000 a 5.000 dominios |
32 GB RAM – 8 vCPU |
5.000 a 10.000 dominios |
64 GB RAM – 16 vCPU |
10.000 a 25.000 dominios |
Note
Para instalaciones corporativas, Planisys entrega un superadmin capaz de crear revendedores, empresas y operadores DNS.
Si no existen revendedores reales, deberá crearse un revendedor ficticio y al menos una empresa para poder asignarle las zonas.
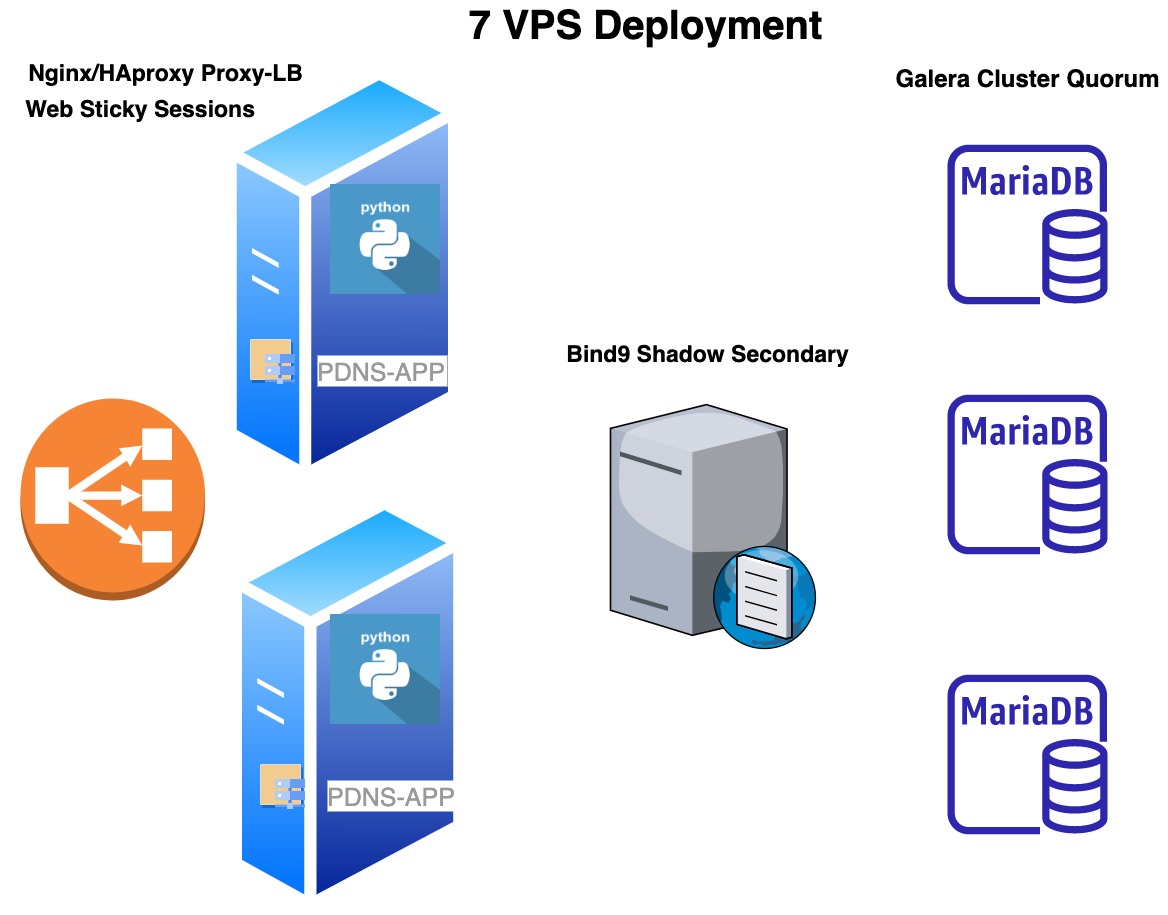
A partir de 20.000-25.000 dominios
Se recomienda infraestructura distribuida:
VPS independientes para: - MariaDB - Bind9 - PDNS-APP
Opcional: Galera Cluster
Load Balancer delante de PDNS-APP
Warning
Para alta disponibilidad, el cliente debe proveer: RAID, doble alimentación A+B, doble upstream, snapshots automáticos, fencing IPMI/DRAC, o Proxmox-HA / VMware-HA según corresponda.
Caso simple — instalación mínima
Pipeline CI/CD — Ansible Jumphost (Pivote)
PDNS utiliza un jumphost (servidor pivote) para:
orquestación Ansible
despliegue automatizado
monitoreo y logs
alertas
CI/CD
Requisito operacional:
Los VPS autoritativos y resolvers deben aceptar
la clave pública SSH del pivote Ansible
en /root/.ssh/authorized_keys
Descripción del concepto NS-SET
Un NS-Set (Nameserver Set) es un conjunto de servidores autoritativos:
1 Master (reconstruye zonas desde base de datos)
N Slaves (reciben replicación)
Características:
Se comparte una llave TSIG (= círculo de confianza anti-spoofing)
Trigger automático al modificar zona: - Genera NOTIFY → Slave hace AXFR/IXFR
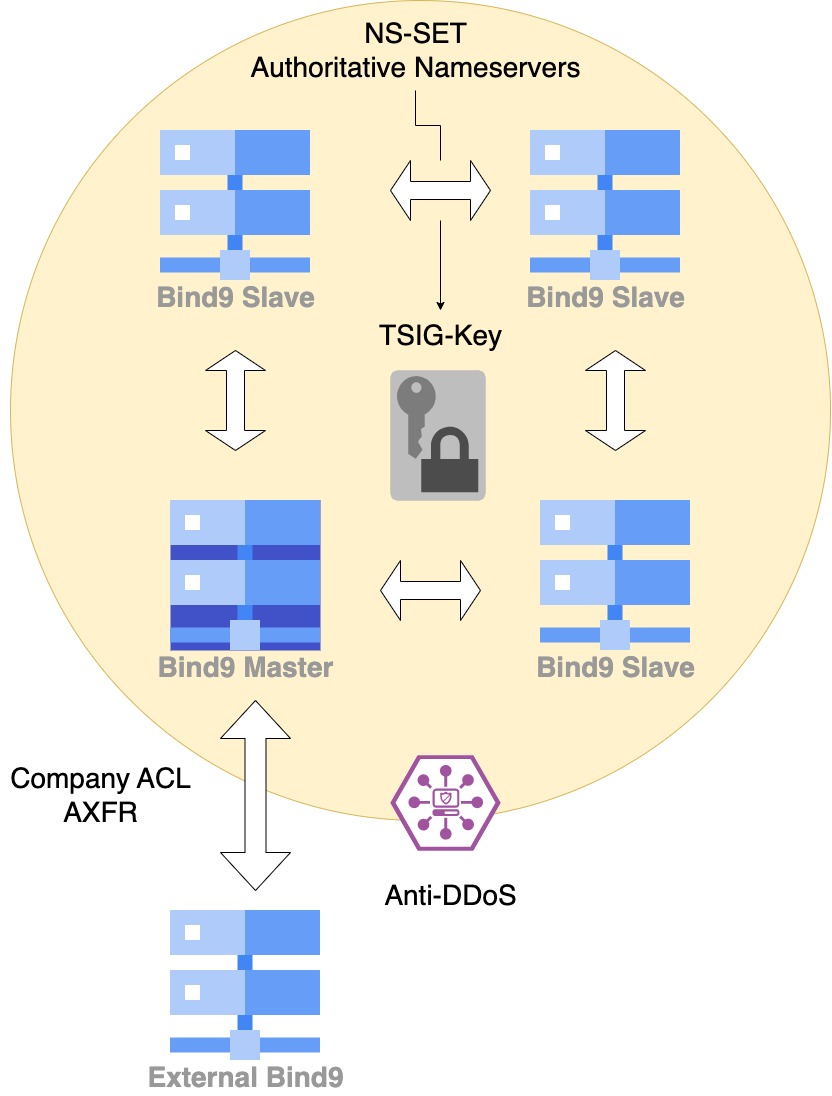
ACLs para transferencias
A nivel empresas se definen ACLs basadas en:
IP
TSIG
combinación IP + TSIG
Esto permite intercambiar zonas con servidores Bind externos.
—