Using dns-suffix for informational redirection
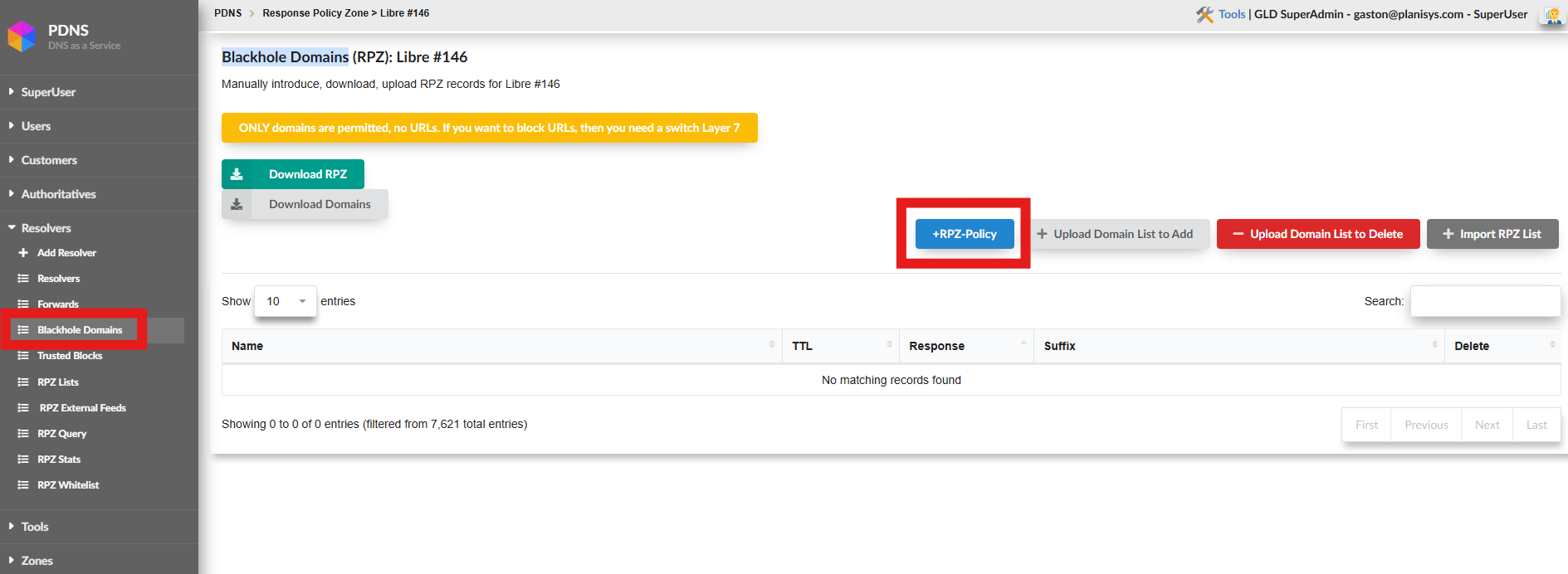
Para poder llegar a esta opcion debemos dirigirnos a la opcion Blackhole Domains que se encuentra en el panel izquierdo dentro de Resolvers. Y desde ahi hacer click en el boton +RPZ-Policy.
En lugar de bloquear un dominio con NXDOMAIN, puede configurarse una política de tipo add-suffix que permita redirigir al usuario a una página informativa (por ejemplo, un portal gubernamental).
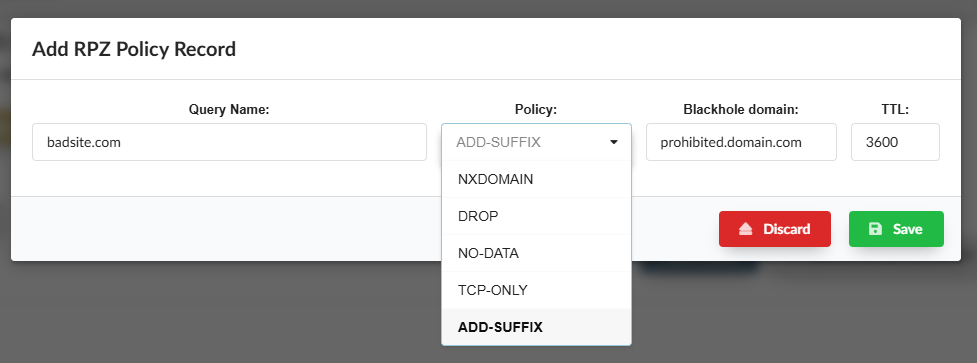
This mechanism works in two parts:
Configuration on the resolver (RPZ): An add-suffix type policy is defined in the Blackhole Domains section. For example, when querying badsite.com, the resolver will respond with a CNAME such as:
badsite.com.prohibited.domain.com.
Configuración en la zona DNS del dominio receptor: En la zona prohibited.domain.com, se debe crear la siguiente entrada wildcard:
* IN A xxx.xxx.xxx.xxx <--(ip del servidor web)
This ensures that any subdomain like badsite.com.prohibited.domain.com resolves to the IP of the web server that will handle the redirection.
Web server configuration (nginx): On the web server responding at xxx.xxx.xxx.xxx, an nginx vhost must be created to capture any subdomain under prohibited.domain.com and redirect it to the desired site.
Below is a full example of nginx.conf:
server { listen 80; server_name .prohibited.domain.com; location / { return 301 https://government-portal.com; } } server { listen 443 ssl; server_name .prohibited.domain.com; ssl_certificate /etc/nginx/ssl/fullchain.pem; ssl_certificate_key /etc/nginx/ssl/privkey.pem; location / { return 301 https://government-portal.com; } }
With this configuration, users attempting to access blocked domains will be redirected to an explanatory page instead of simply receiving a DNS error.
Configurar certbot para la generacion de certificados
Se detallan los pasos a seguir en Debian para la generacion de certificados SSL para ser puestos en Nginx
apt install certbot
Instalar un servidor en una IP p.ej. 1.2.3.4
Poner un registro A de servidor.dominio.com apuntando a 1.2.3.4
Poner un registro CAA que diga “issue 0 letsencrypt.org”
El puerto 80 debe estar libre de firewall
Ejecutar:
systemctl list-timers | grep certbot
Esto es para para asegurarse que haya un timer de renovación de certbot.
Editar el siguiente archivo:
/etc/letsencrypt/renewal-hooks/deploy/reload-nginx.sh
chmod +x /etc/letsencrypt/renewal-hooks/deploy/reload-nginx.sh
Dentro de ese archivo poner:
#!/bin/bash
cp /etc/letsencrypt/live/servidor.dominio.com/fullchain.pem /etc/ssl/certs/fullchain.pem
cp /etc/letsencrypt/live/servidor.dominio.com/privkey.pem /etc/ssl/private/privkey.pem
systemctl reload nginx
Dentro del nginx configurar:
server {
listen 443 ssl;
server_name ~^(.+\.)*servidor\.dominio\.com$;
ssl_certificate /etc/ssl/certs/fullchain.pem;
ssl_certificate_key /etc/ssl/private/privkey.pem;
return 301 https://servidor.dominio.com$request_uri;
}
server {
listen 443 ssl http2;
server_name servidor.dominio.com;
ssl_certificate /etc/ssl/certs/fullchain.pem;
ssl_certificate_key /etc/ssl/private/privkey.pem;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256';
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload" always;
location / {
root /var/www/html;
index index.html index.htm;
}
}