Response Policy Zones
Introduction
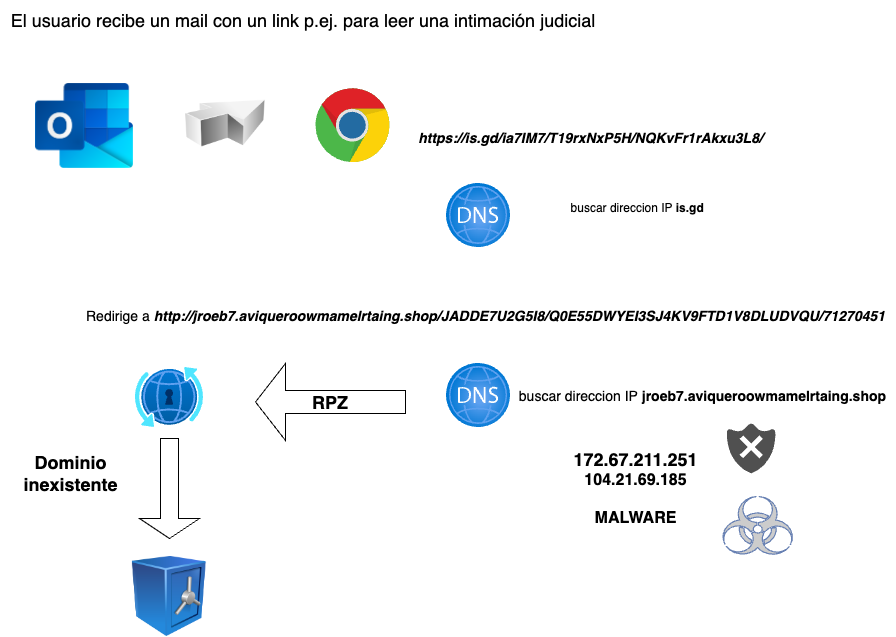
RPZ is a feature of resolvers that allows listing domains that should not be accessible by the user or system using that resolver.
This can be due to a court order, a censorship action, or, most commonly, a cybersecurity measure associated with endpoint protection.
In other words, when a user receives an email with a malicious link, or when a user’s PC is infected with malware that needs to access a Command & Control domain, if their resolver is on an IP of a Resolver RPZ provided by Planisys, it is likely that access to that domain will be blocked, and the danger will disappear because the malware or Command-and-Control server cannot be reached.
Resolvers
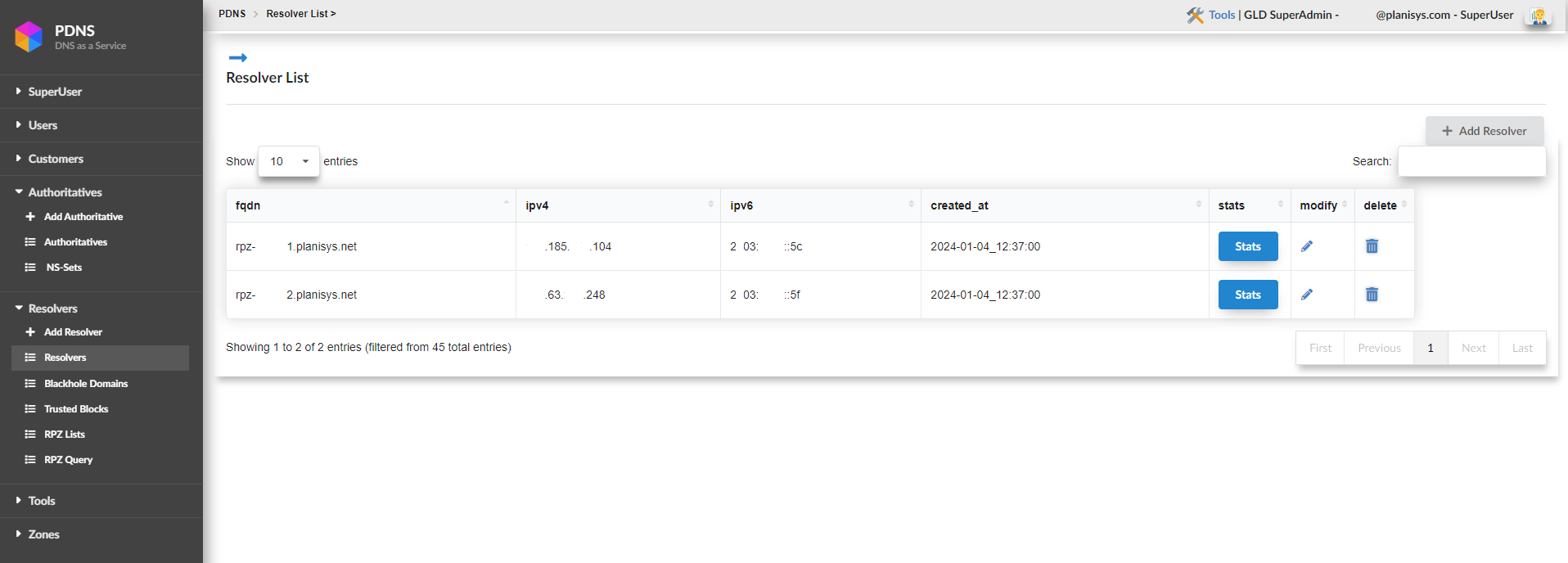
One of the first screens we encounter is the resolvers screen. Here, the resolvers that have been assigned to us and need to be configured in our environment are listed.
Per-resolver statistics
By clicking on STATS, we can view various statistics of our resolvers.
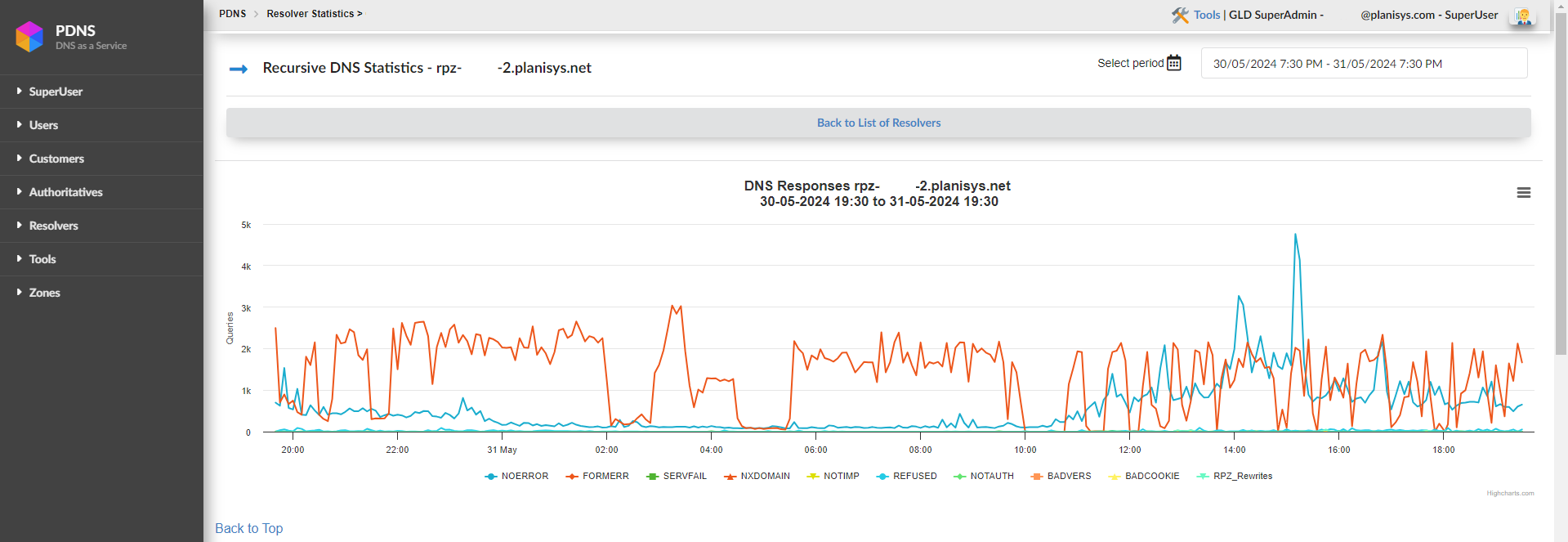
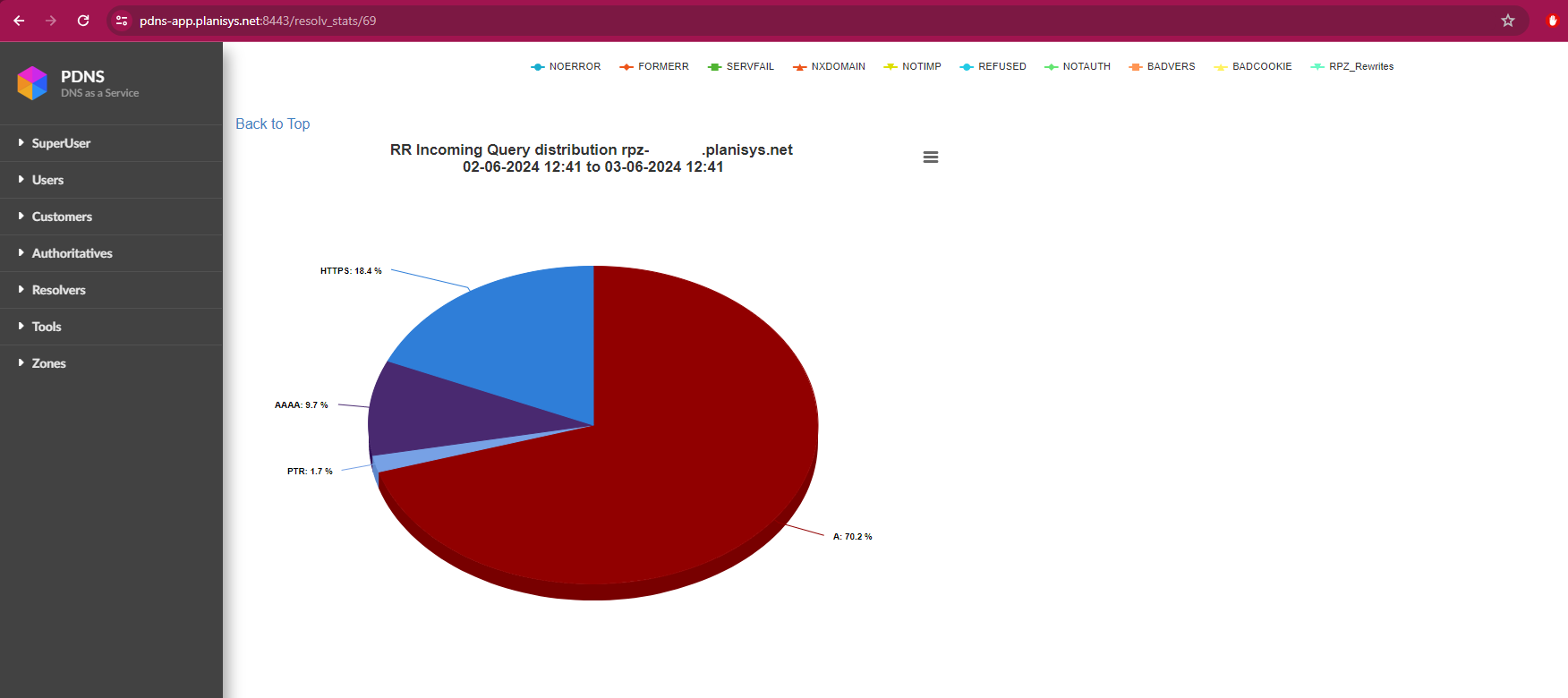
Below are the response codes that can be generated when making a query to a BIND9 server, which we can observe at the bottom of the graphs:
NOERROR: Indicates that the DNS query was successful. The server was able to resolve the domain name and return a valid response.
FORMERR (Format Error): The DNS server indicates that it received a malformed query. This means the request sent does not comply with DNS protocol specifications.
SERVFAIL (Server Failure): El servidor DNS no pudo procesar la consulta,es una respuesta generica cuando algo ante un formato o comando que no es para DNS.
NXDOMAIN (Non-Existent Domain): Indicates that the requested domain name does not exist in the DNS. The server is reporting that there are no records for that domain.
NOTIMP (Not Implemented): El servidor DNS no admite el tipo de consulta o la operación solicitada.
REFUSED: The DNS server refuses to process the query. This can happen for several reasons, such as security restrictions or server configuration to reject queries from certain IP addresses.
NOTAUTH (Not Authorized): The DNS server is reporting that it is not authorized to provide a response for the zone in question. This can occur if the query is directed to a server that is not authoritative for the requested zone.
BADVERS (Bad Version): This code indicates that the query used an incompatible or incorrect version of the DNS protocol.
BADCOOKIE: This is related to DNS cookie validation, used in DNS Cookies to protect against denial of service (DoS) attacks. This error occurs when the received DNS cookie is invalid or does not match what the server expected.
RPZ_Rewrites: “RPZ” refers to Response Policy Zones, a BIND feature that allows DNS responses to be overridden based on policies. When you see “RPZ_Rewrites”, it means the DNS server has modified the response according to policies defined in an RPZ zone, such as blocking certain domains or redirecting them.
Unified statistics of the resolvers
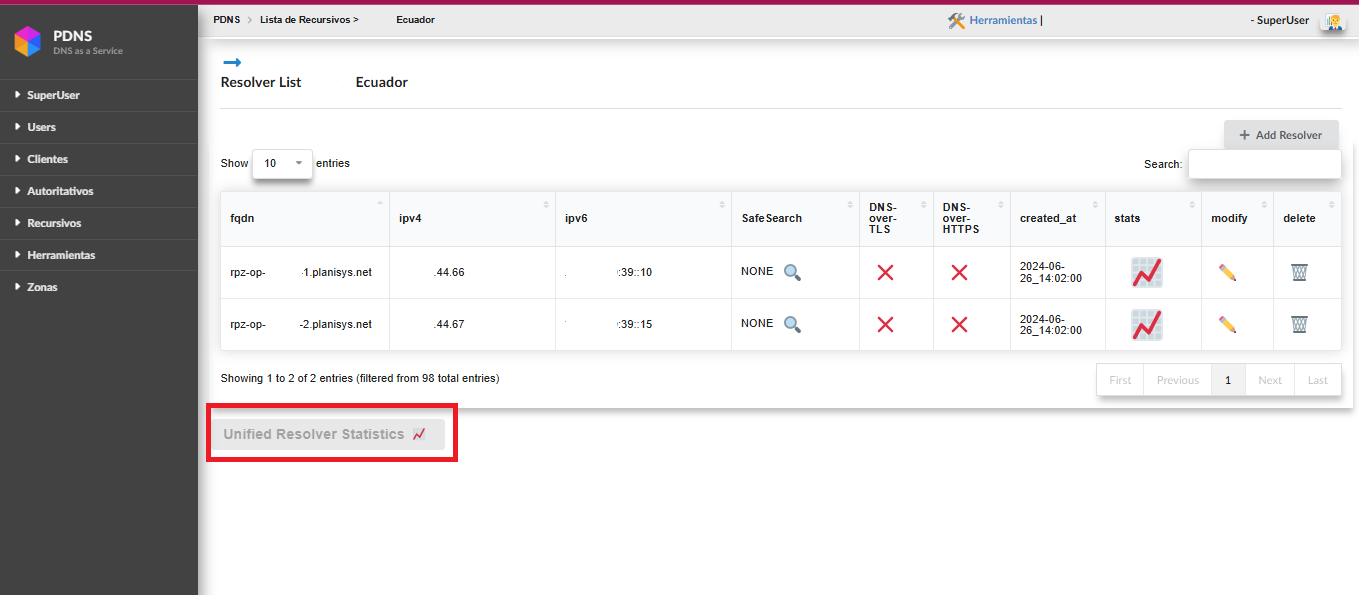
Below the list of resolvers, a new button has been added where the following statistics can be observed. These statistics are the result of the sum of all resolvers.
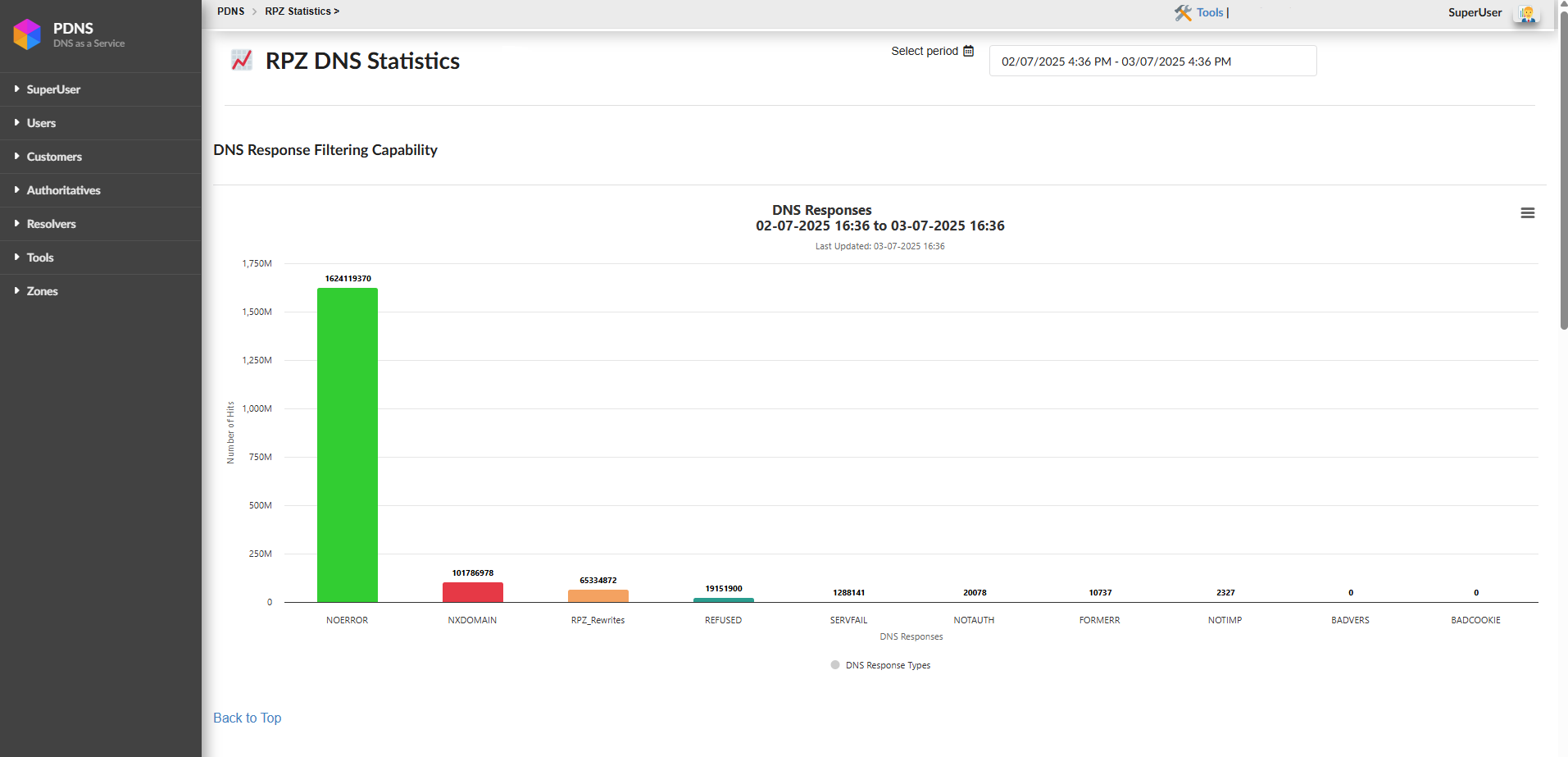
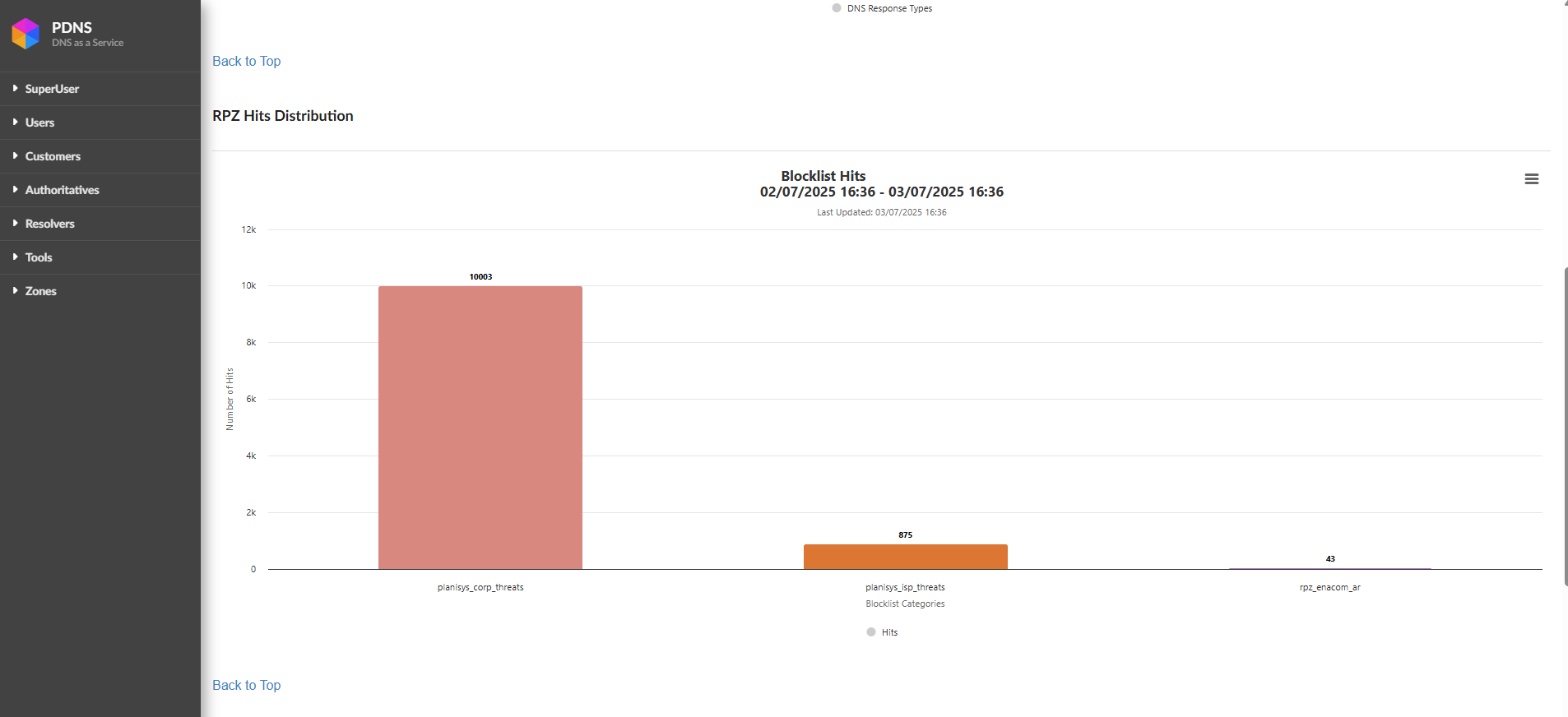
Top 100 RPZ Hits Report
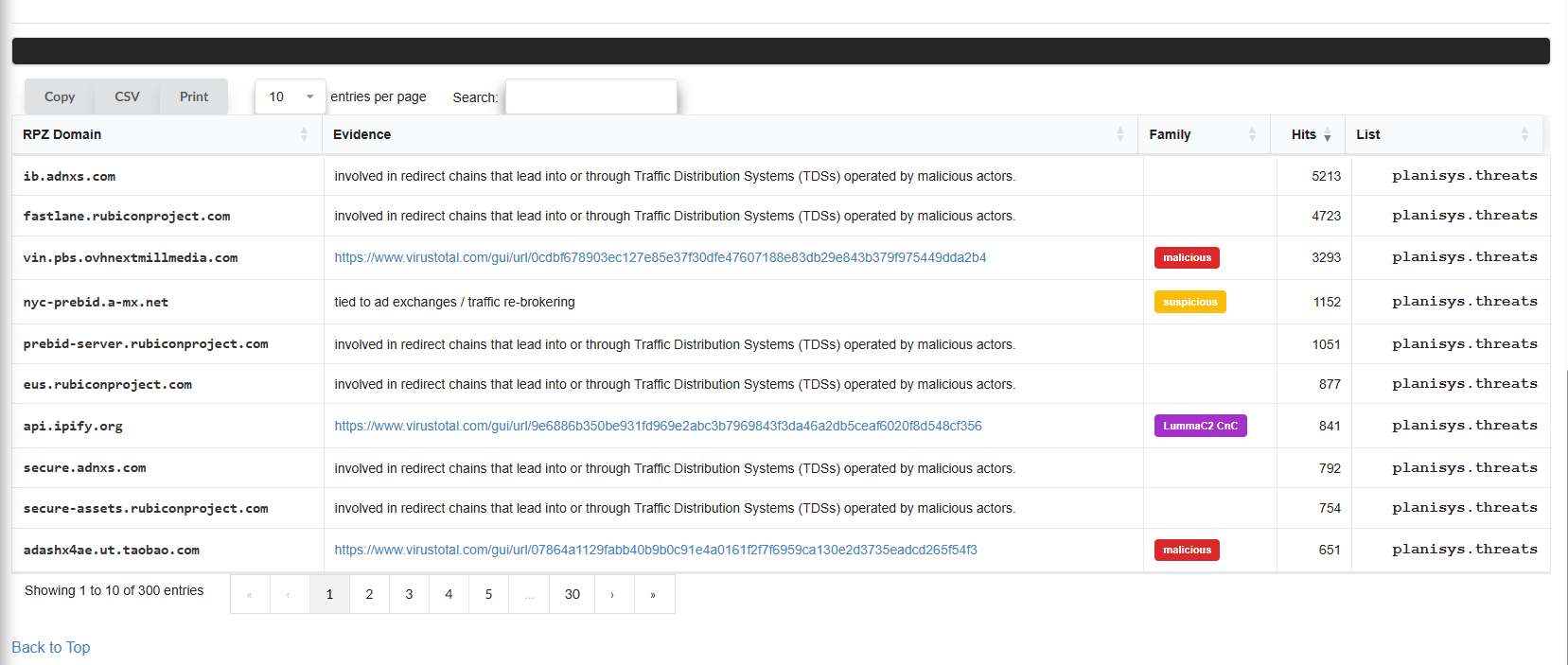
Below the graph, a table is shown with the top 100 domains/IPs that have generated the most hits in the continuous analysis performed by the DNS RPZ during a given period.
This table includes three main columns:
RPZ Domain: The domain that has been blocked due to its association with malicious or suspicious activities.
Hits: The number of times that domain has been queried and blocked.
List: Shows the details of the involved IP addresses, following the RPZ-IP format.
This table is updated periodically and reflects the most relevant domains in terms of malicious or unwanted activity.
About RPZ-IP Addresses
For example, an entry like:
32.82.31.17.85.rpz-ip
Can be interpreted as follows:
The number “32” indicates a /32 prefix, which refers to a specific IP that has been blocked.
The rest of the address is inverted, meaning the associated IP would be
85.17.31.82.
In other cases, like:
12.0.0.0.223.rpz-ip
The number “12” refers to a CIDR block /12, which covers a range of IP addresses, in this case 223.0.0.0/12. If a query attempts to resolve within this block, it will be blocked and return an NXDOMAIN.
In summary, the Top 100 hits table shows us the main vectors detected by RPZ. It blocked access to malicious destinations and protected both the network and its users. Understanding how to interpret the associated addresses and blocks is key to keeping your network protected from potential threats.
Blackhole Domains
Here, you can manually enter, upload, and download records for our RPZ.
In the case of files containing a large number of domains, such as those provided by the government, they can be uploaded without issues related to the size or duration of the process. Additionally, this screen displays a progress bar to facilitate tracking the upload
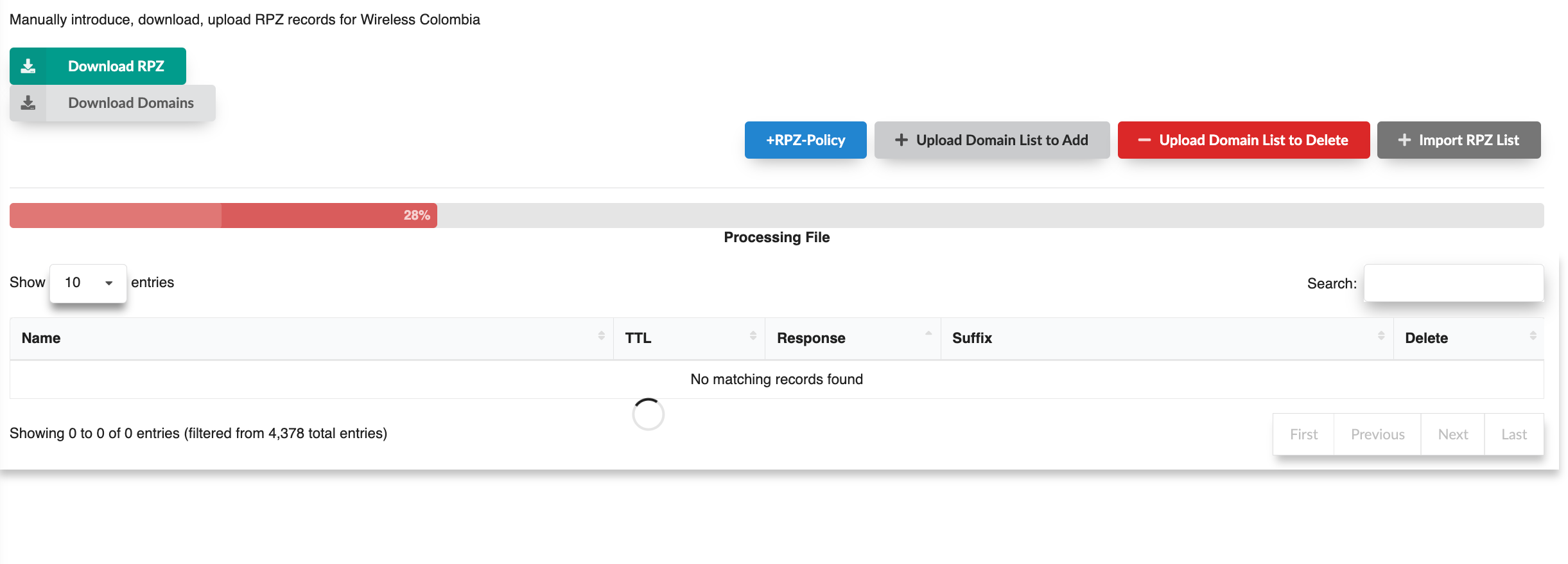
Important!! To activate this, you need to have the list: rpz_local enabled, which is located in RPZ List as shown in the following screenshot:
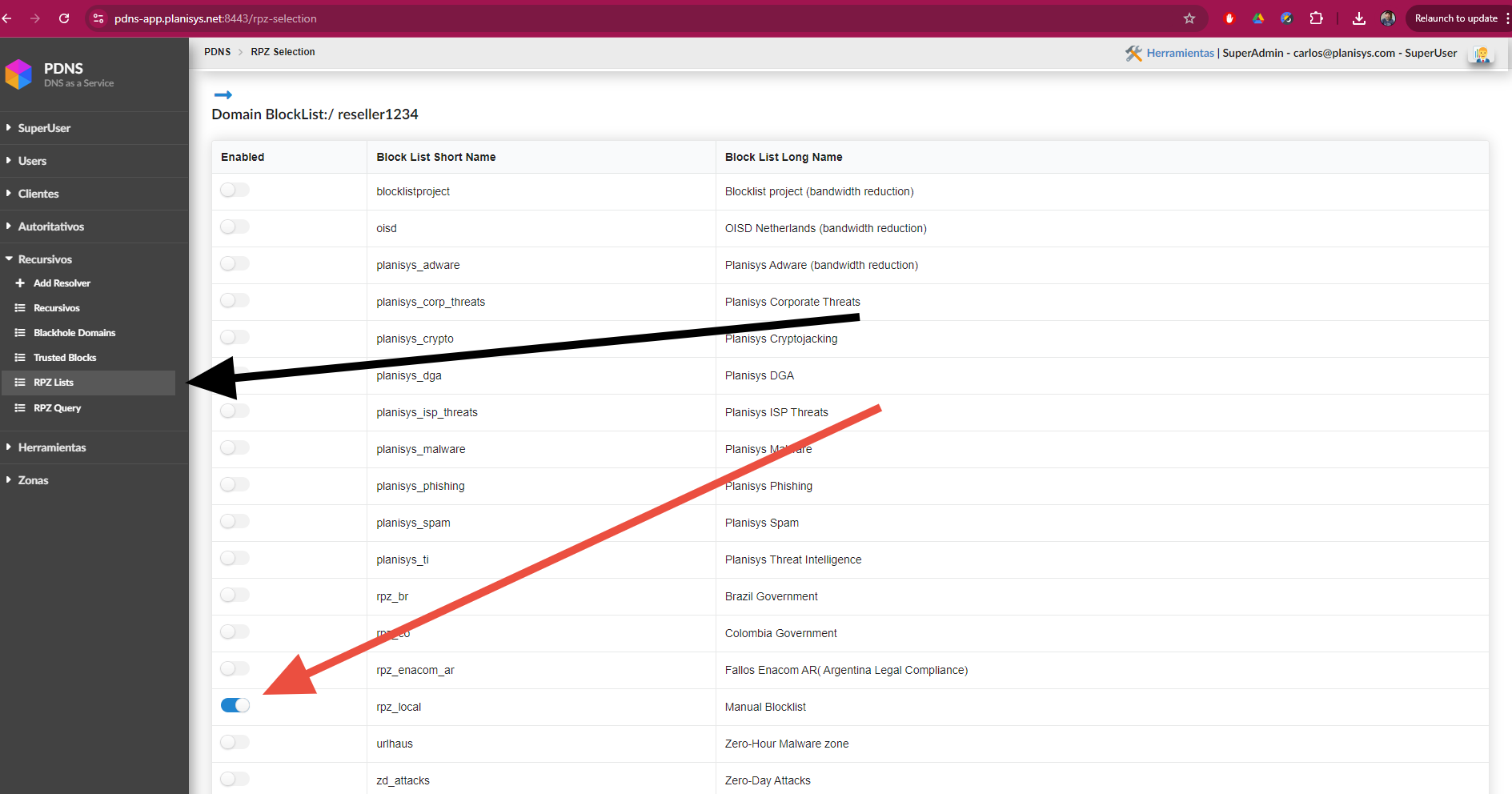
Trusted Blocks
This screen contains the list of CIDR blocks allowed to use the resolvers. With the “Add IPv4 CIDR” and “Add IPv6 CIDR” buttons, you can add IP ranges or specific IPs.
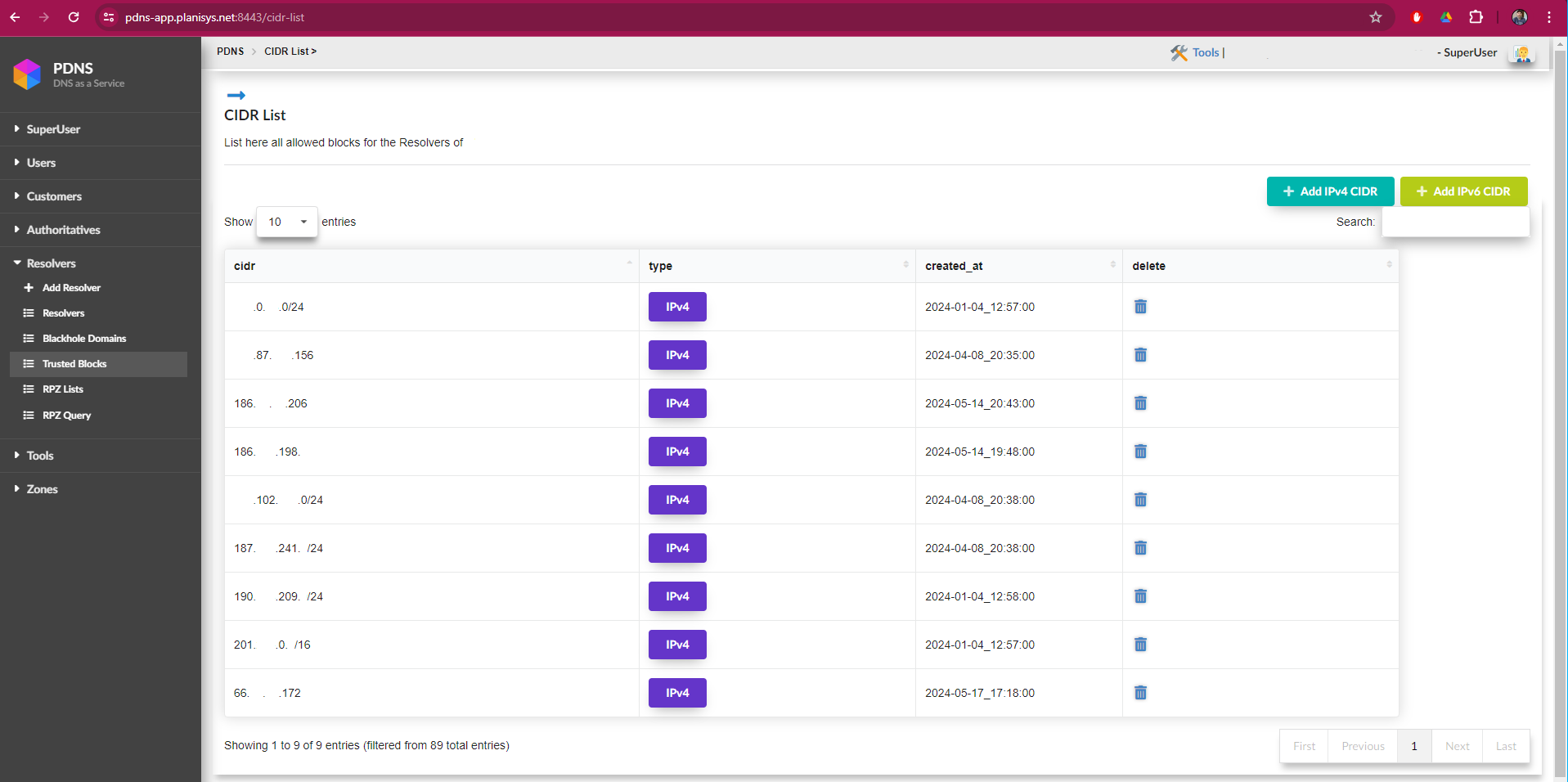
RPZ List
This screen contains all the lists and categories that are part of the DNS Response Policy Zones (RPZ) security service. These lists are constantly updated by Planisys Threat Intelligence and its SOC, which is responsible for keeping information up to date on threats, dangerous sites, and advertising. Thus, the ISP can enable or disable the lists according to the level of security they wish to implement.
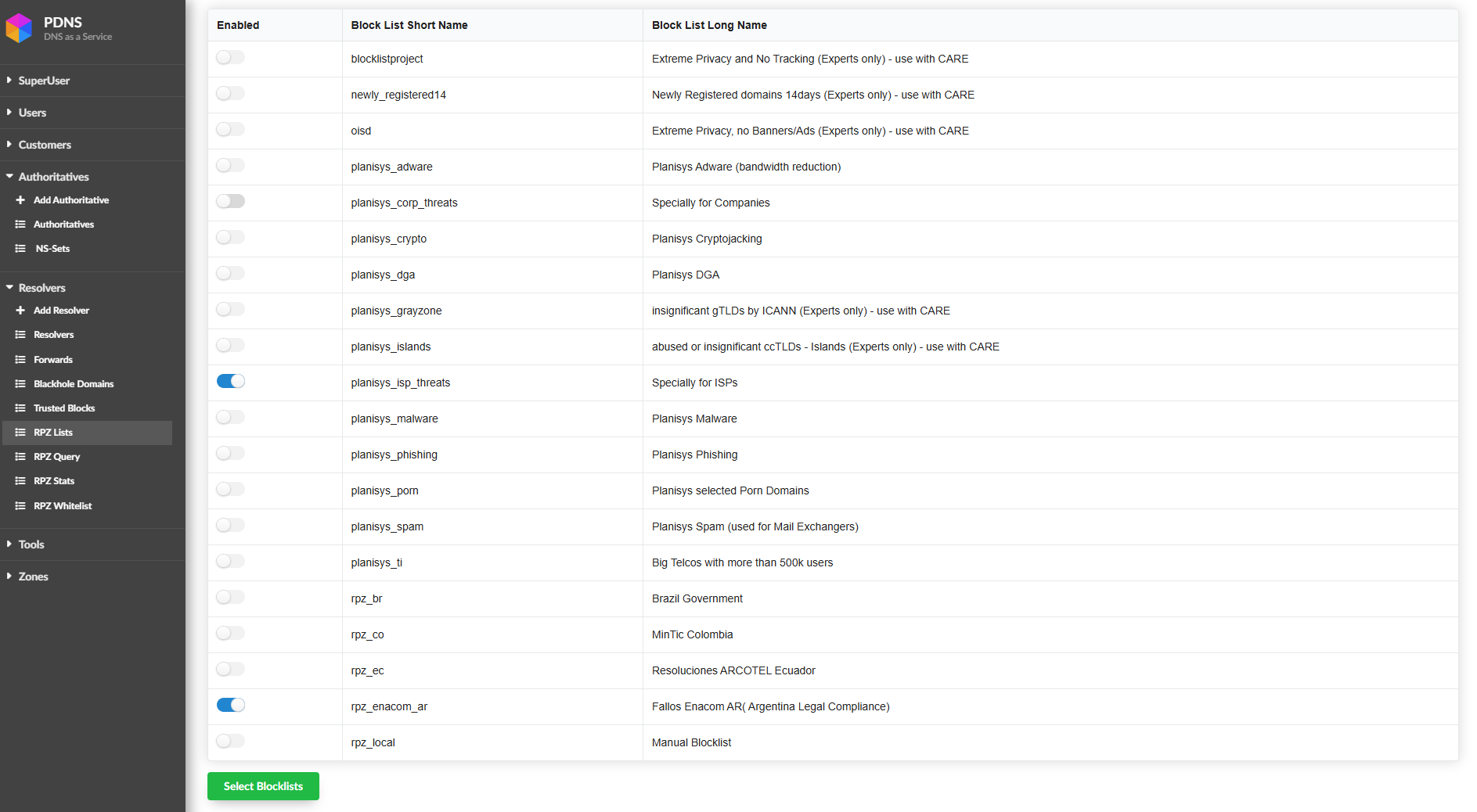
Warning
Esta imagen sirve de ejemplo de como deberia configurarse un ISP Argentino con menos de 500 mil abonados.
Se agregaron las siguientes listas, a continuacion una descripcion de las mismas:
newly_registered14 Newly Registered domains 14days Cambia todos los días una vez por día y tiene los dominios registrados en los últimos 14 días, que en gran cantidad de casos se usan para el cibercrimen.
planisys_grayzone cheap, abused or insignificant gTLDs by ICANN Son dominios baratos que se usan mucho en cibercrimen como .top, .xyz , etc.
planisys_islands abused or insignificant ccTLDs - Islands.
Esta lista contiene global Top-Level-Domains correspondientes a islas que no tienen infraestructura Internet, pero ponen sus dos letras a disposición para hacer dinero con Registries que venden subdominios.
Esos nombres han sido abusados por hackers provocando una alta curva de cibercrimen. No es necesario que lo prendan, solo en caso de encontrar en los reportes muchos ataques de nombres terminado p.ej. en ac o me o similar.
La siguiente es un extracto de la lista de:
*.bl IN CNAME . ; Saint Barthélemy *.bv IN CNAME . ; Bouvet Island (uninhabited) *.cx IN CNAME . ; Christmas Island *.eh IN CNAME . ; Western Sahara *.fk IN CNAME . ; Falkland Islands *.fo IN CNAME . ; Faroe Islands *.gf IN CNAME . ; French Guiana *.gl IN CNAME . ; Greenland *.gp IN CNAME . ; Guadeloupe *.gs IN CNAME . ; South Georgia and South Sandwich Islands *.hm IN CNAME . ; Heard and McDonald Islands *.je IN CNAME . ; Jersey *.mf IN CNAME . ; Saint Martin *.nf IN CNAME . ; Norfolk Island *.pm IN CNAME . ; Saint Pierre and Miquelon *.pn IN CNAME . ; Pitcairn Islands *.sh IN CNAME . ; Saint Helena and Ascension *.sx IN CNAME . ; Sint Maarten *.tc IN CNAME . ; Turks and Caicos *.vg IN CNAME . ; British Virgin Islands *.wf IN CNAME . ; Wallis and Futuna *.yt IN CNAME . ; Mayotte
Warning
Nos hemos encontrado que Microsoft está utilizando aka.ms, por lo que hemos eliminado al *.ms de la lista de islas, así como *.gl que ya sabemos de antemano que Google lo había usado
RPZ Query
With the RPZ Query functionality, the operator can perform support tasks and verify if a domain is being filtered by the service in response to a customer’s request. This facilitates support, and if a known domain is being mistakenly filtered, the screen will indicate which list is filtering it, allowing you to disable it and/or report it if necessary.
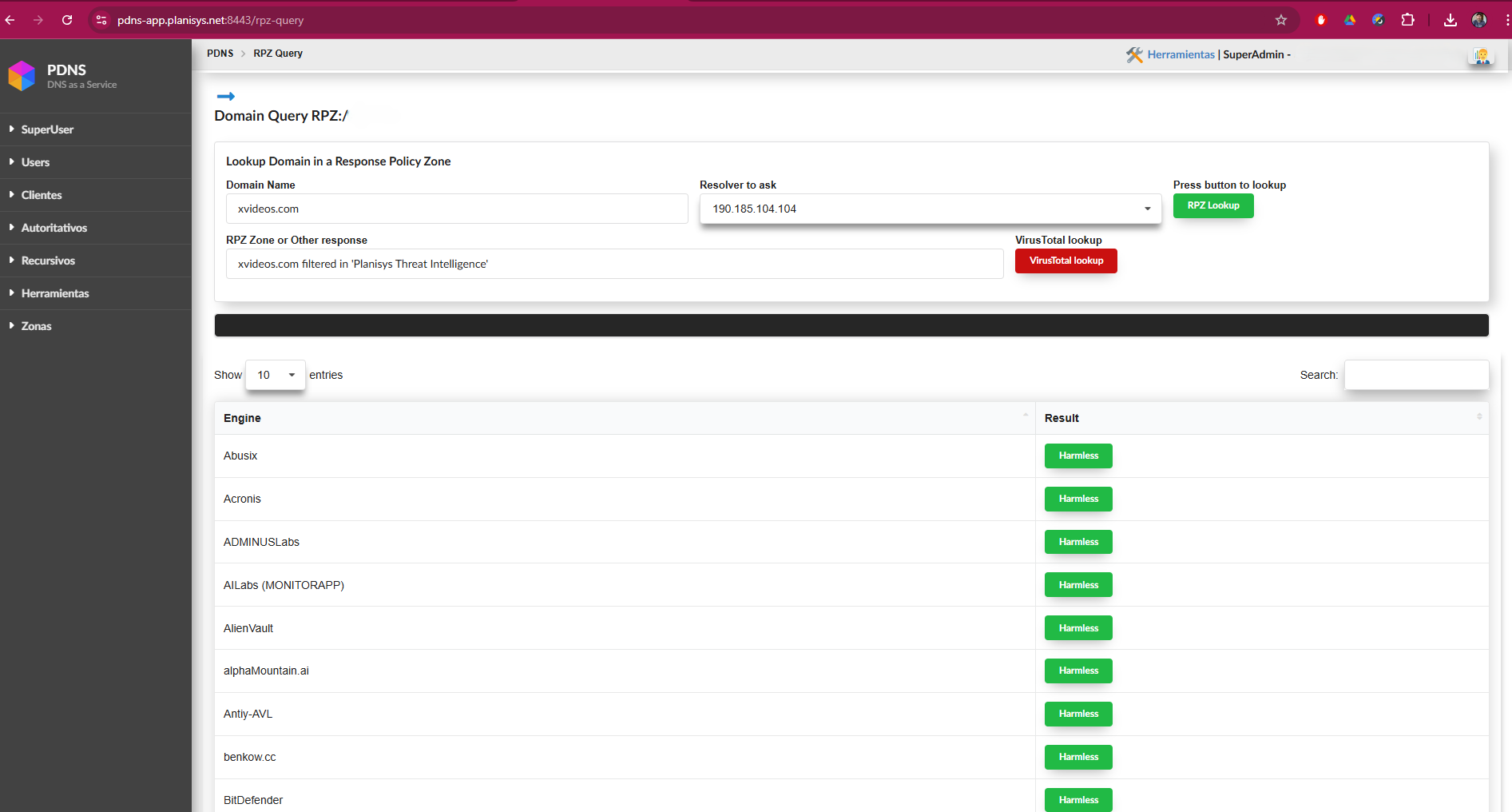
In the picture, we can see that under Domain Name, we enter the site to search/review. And under RPZ Zone or Other Response, we see if the domain in question is filtered by our service. If it is filtered, it appears as shown in the picture, explaining which list it was filtered by. This allows us to disable the list if necessary. If the domain is not listed, it would say: is not RPZ filtered.
With the latest system update, a new button called “VirusTotal Lookup” has been added. This button, available once the site has been listed in one of the RPZ lists, allows a direct search in VirusTotal. This feature enables us to evaluate the reputation of the site in question by consulting the results provided by all the security providers collaborating with VirusTotal. This integration facilitates a thorough review of the domain’s security status, giving us an additional tool to protect our network.
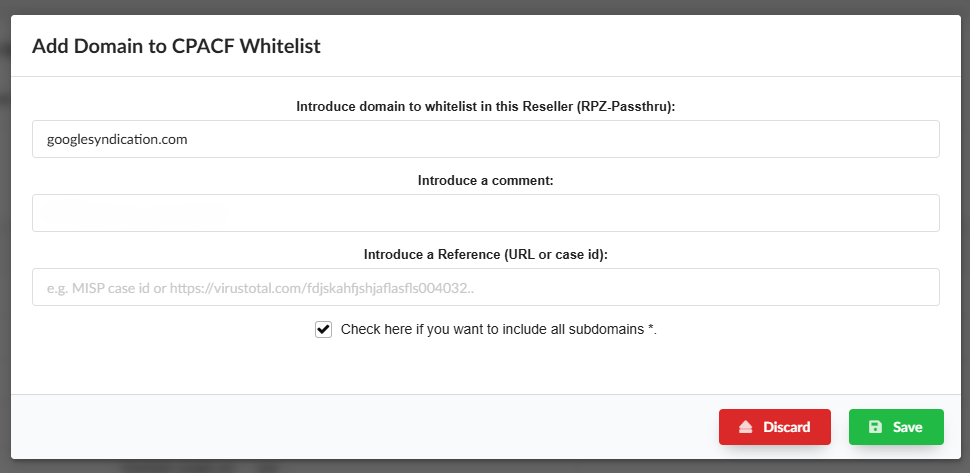
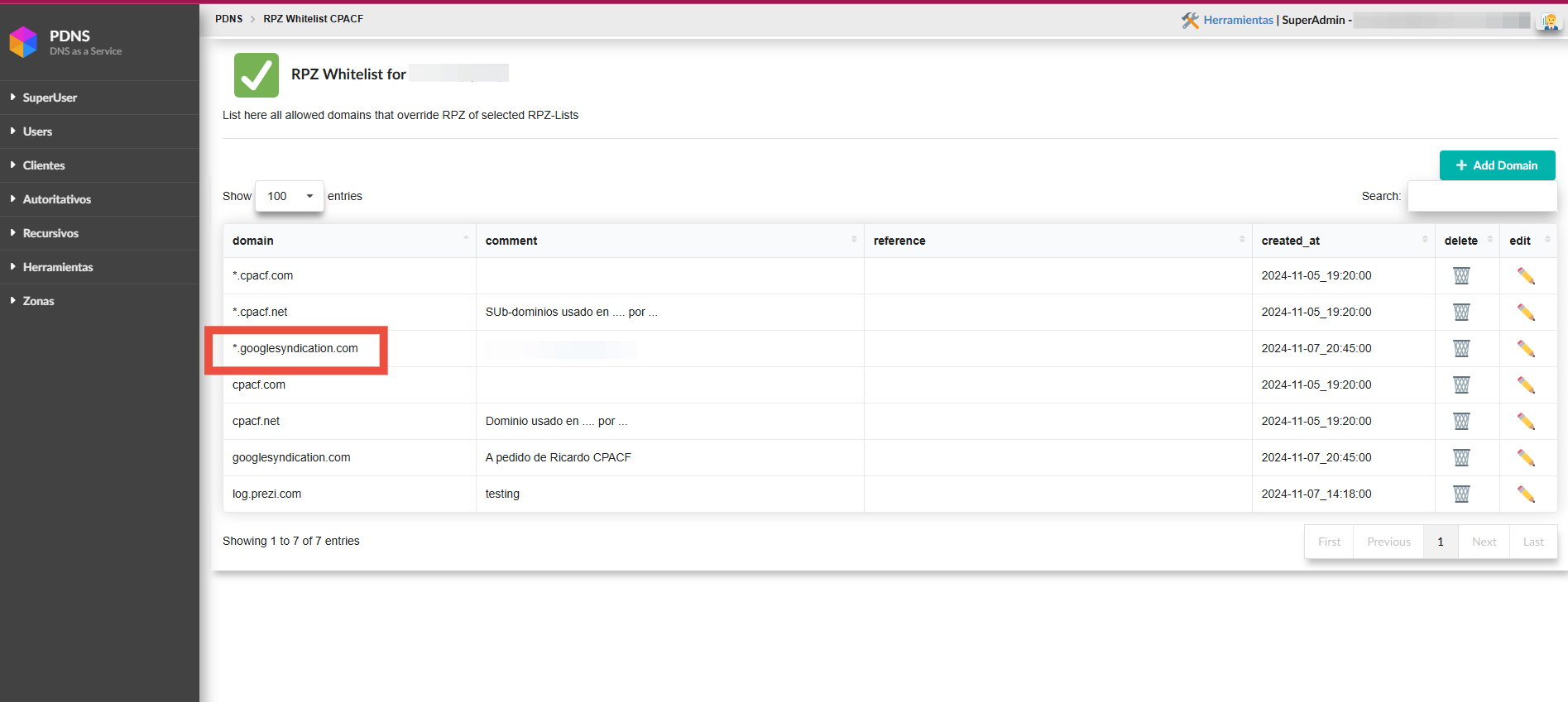
RPZ Whitelist
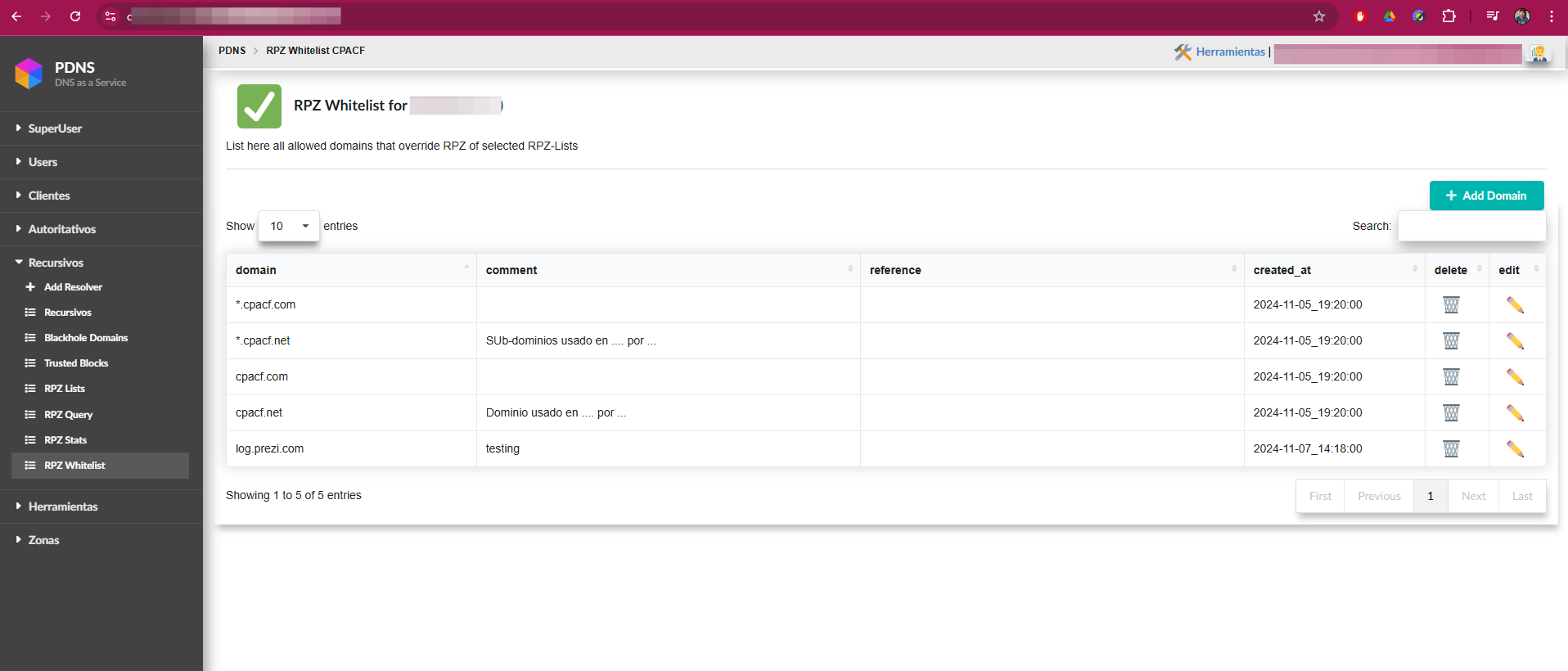
On this screen, the operator has the option to add one or multiple domainsthat will bypass any of the RPZ-Lists where they are listed. This allowsfor efficient management of exceptions, ensuring that the specified domainsare not blocked by the active protection lists. Additionally, the operatorcan manage these exceptions to ensure that security policies are tailored to the specific needs of the network.
In the following example, we see how to list all the subdomains forgooglesindication.com, as shown in the next screen: